Now that we’ve both covered the different layer 1 and layer 2 frame formats, let’s dig into how these frames actually work to connect and roam to Wi-Fi networking.
When joining a BSS, the first step is discovering which BSSs are available. As discussed earlier, this is accomplished through beacon announcements, transmitted at specific time intervals known as the Target Beacon Transmission Time (TBTT), or simply the beacon interval.
To capture beacon frames, you’ll need a wireless capture device tuned to the correct channel. Note that AP packet captures often don’t include their own beacons—this is certainly the case with the Extreme Networks APs I regularly use. Each beacon frame contends for the wireless medium, and when multiple SSIDs are in use, this contention creates overhead as multiple beacon frames are transmitted.
This issue is mitigated in 6 GHz with the introduction of the Multiple BSSID element. The CWAP-404 book doesn’t dive into this in detail, but Rasika Nayanajith covers it brilliantly in his post.
As I mentioned in my Chapter 4 post on 802.11 MAC frames, joining a BSS follows a defined sequence known as the 802.11 state machine. Here’s a closer look at what we can observe in these frames.
Probe Request
A probe request frame is sent by the client to discover BSSs. It can be triggered in two scenarios:
- Passive Scanning: The client responds to SSIDs learned from beacon frames.
- Active Scanning: The client sends requests without prior knowledge of whether the SSID is broadcast (common with hidden SSIDs).
Probe requests reveal the capabilities of the client device, such as support for HT, VHT, or HE. However, just because a device supports HE doesn’t mean it supports all HE features. Other valuable insights include the number of spatial streams, supported channel widths, and data rates (MCS).
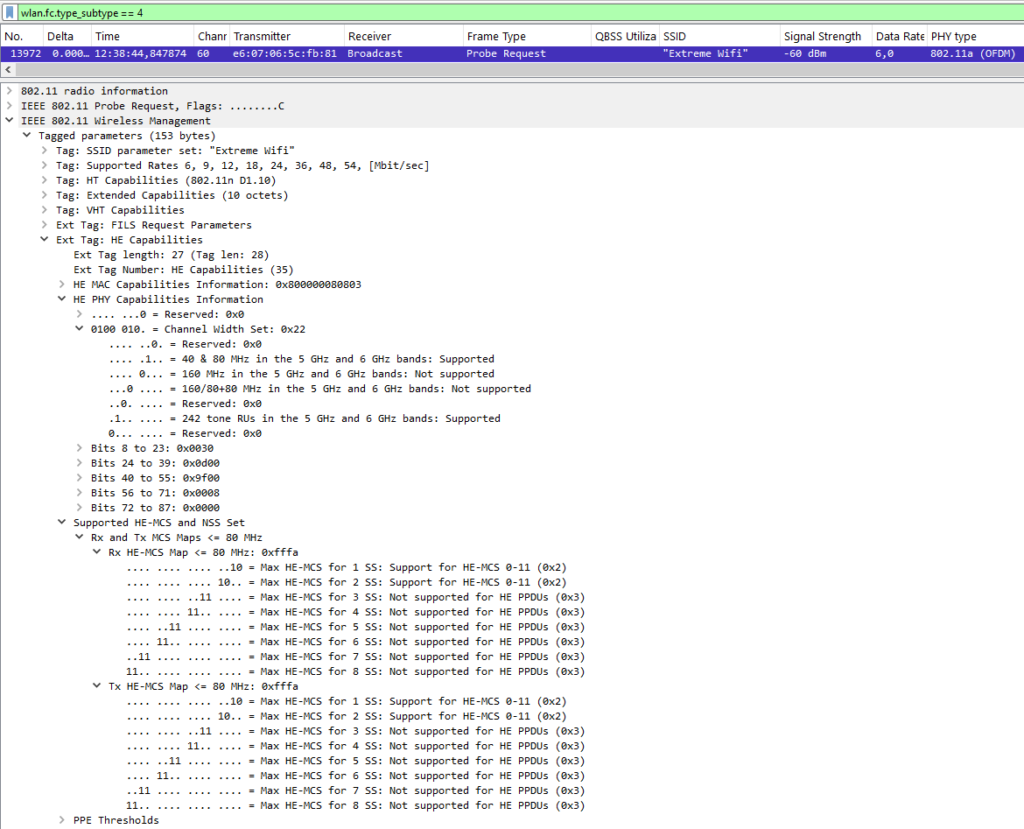
In this screenshot, you can see that the device supports HE, has 2 spatial streams (SS), and supports 80 MHz channels but not 160 MHz. You can dive into HT and VHT capabilities for a complete picture, but for brevity, I’ve skipped additional screenshots.
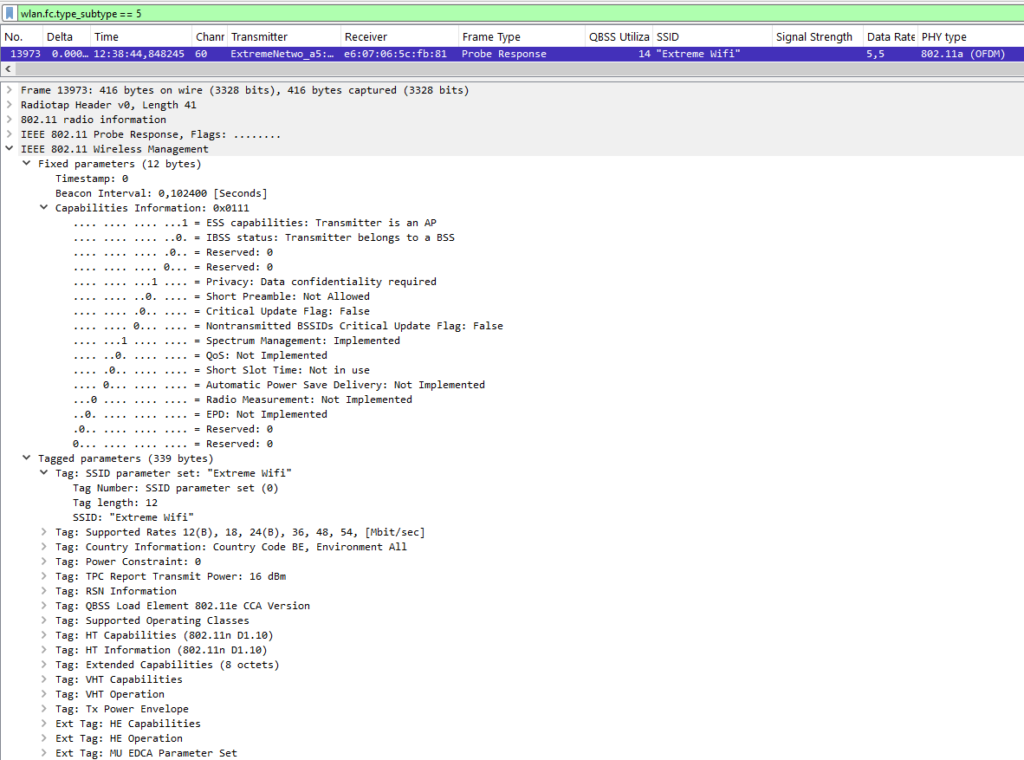
Probe Response
After a request, the AP responds with a probe response. This frame mirrors much of the information in beacon frames but omits elements such as:
- Traffic Indication Map (TIM)
- QoS Capability Element
- AP Channel Report Element
If the client requested specific elements, the AP will include them in the response.
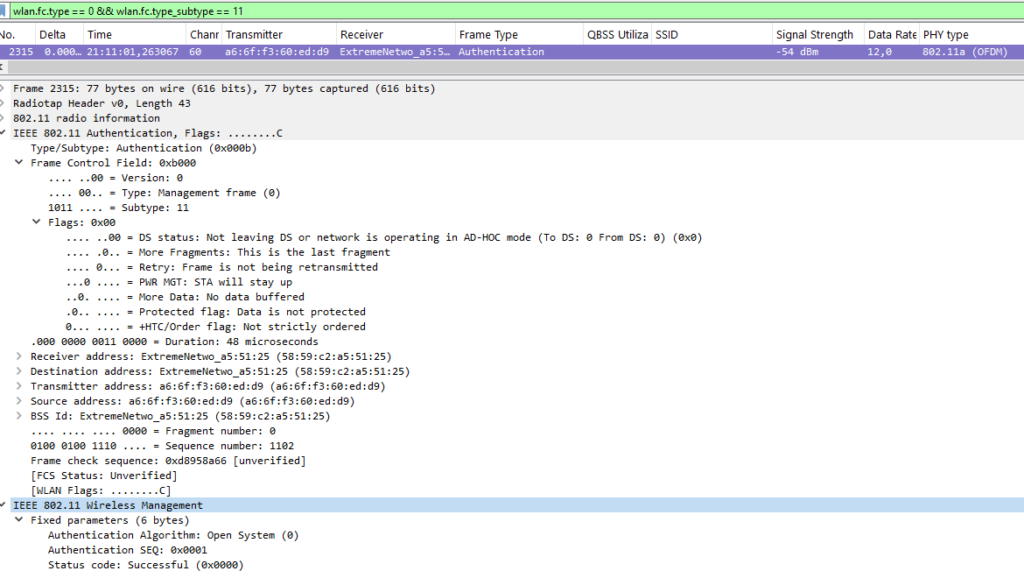
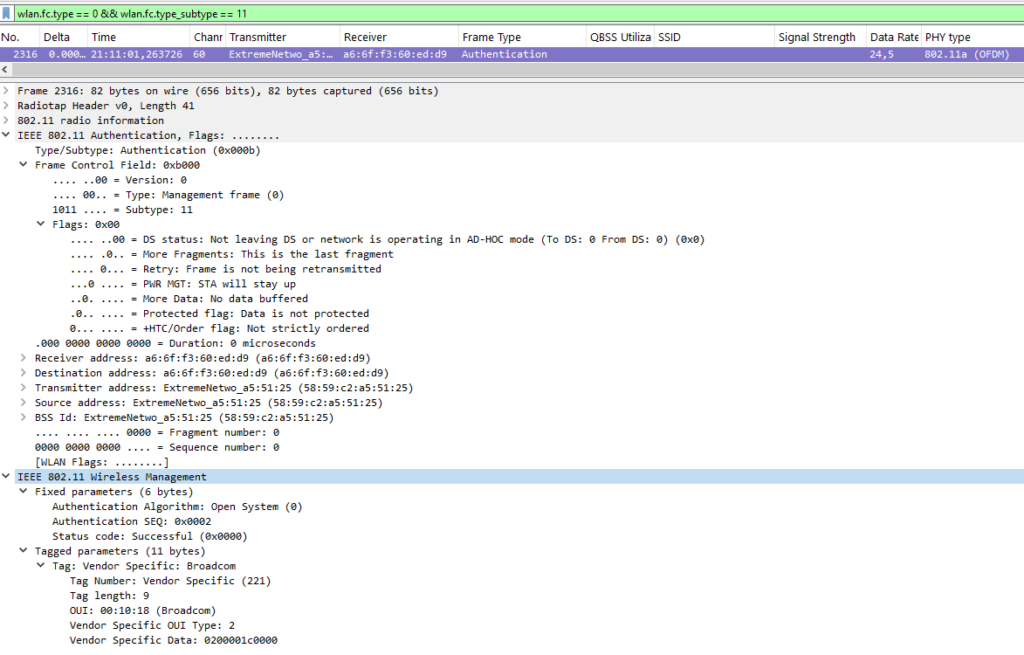
Authentication Exchange
The authentication process begins with the STA sending an authentication frame to the AP, followed by a unicast response from the AP. For WPA2 networks, this is typically “open authentication,” which shouldn’t be confused with the 4-way handshake where the actual PSK exchange occurs.
The key fields in these frames are:
- Authentication Algorithm Number: (0 = Open)
- Authentication Sequence: (1 or 2)
- Status Code: (0 = Successful; other values indicate failure reasons).
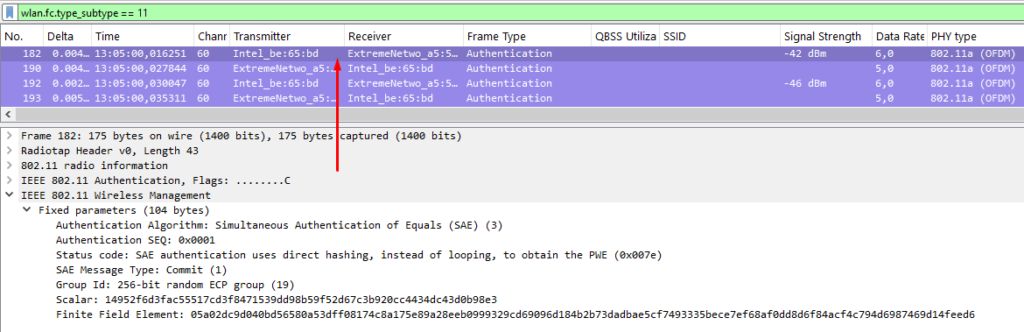
In WPA3-SAE, the algorithm changes to 3 (SAE), and the exchange involves four frames rather than two. Additional security elements are also present in the frame body.
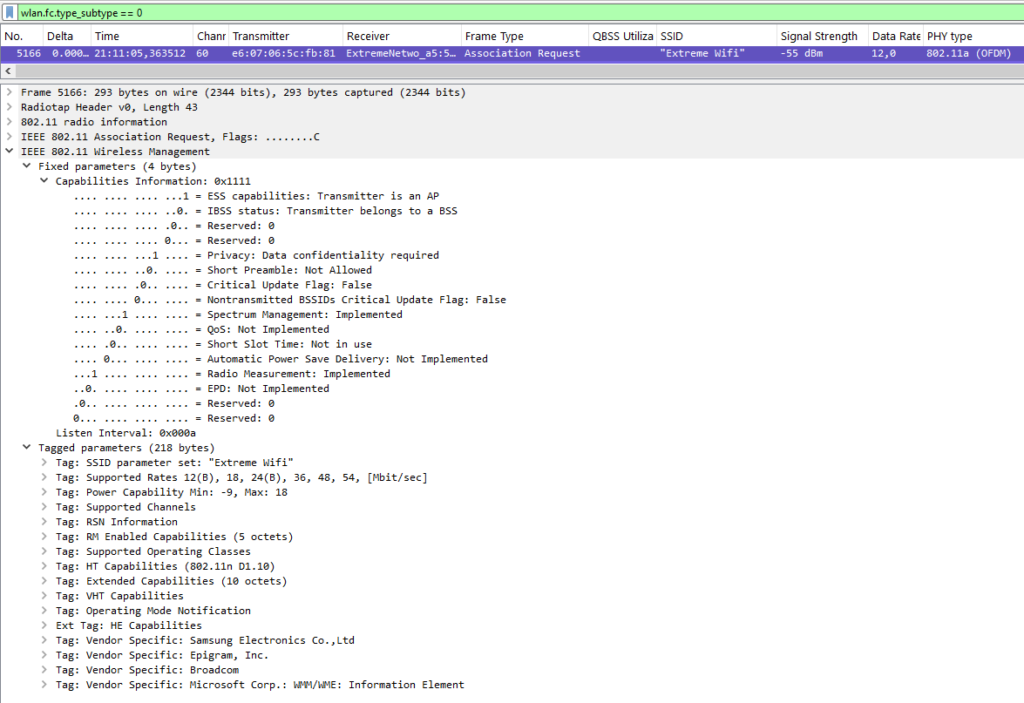
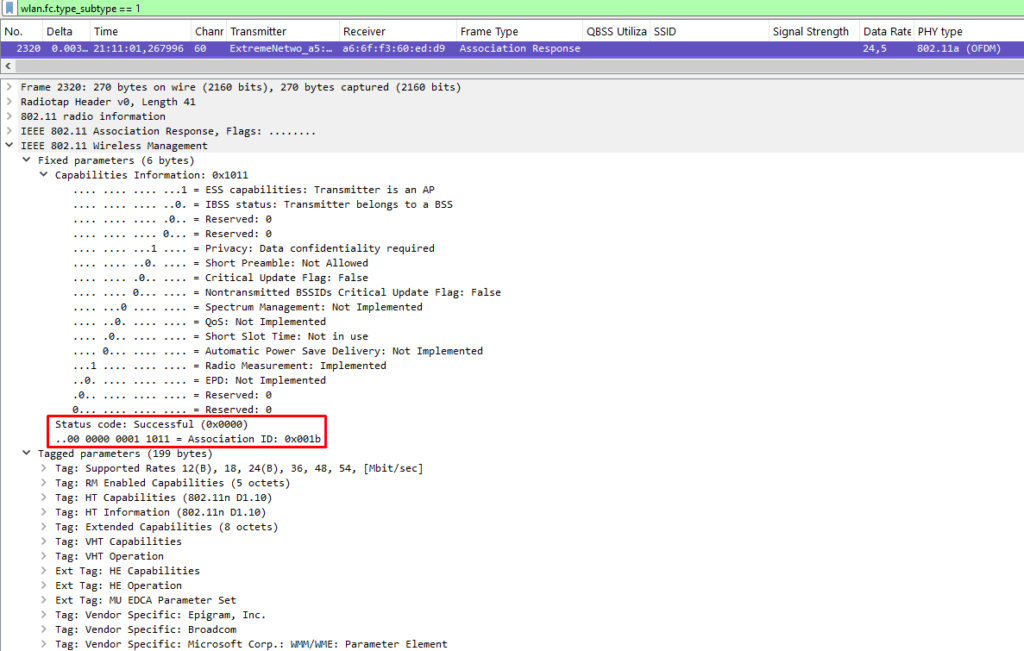
Association
At this stage, after probing and authenticating—or “showing off and greeting”—the client device sends an association request to the AP. In this request, the client once again includes its capabilities, while the AP responds with what capabilities and features it will use during the connection.
The association response typically contains more optional fields than the request. This is because the AP not only replies to the client’s requested capabilities with its own but also includes fields like HT, VHT, and HE operation elements. Additionally, the AP may inform the client of other BSS-related information, such as Overlapping BSS Scan parameters, the BSS Max Idle Period (used with 802.11v), and Neighbour Reports (802.11k).
The two most important fields in the response are found at the beginning of the frame:
- Status Code: Indicates whether the association was successful or not. If unsuccessful, a reason code is attached.
- Association ID (AID): Used to identify the client in the BSS, especially for power-saving mechanisms. For example, buffered data in beacon frames (TIM) is tied to the AID.
802.11 Security
If you’re connecting to an open SSID, the association exchange completes the process. However, this leaves your data unprotected, making it easy to capture using any wireless NIC in monitor mode. For secure connections (WPA2/WPA3), encryption is established through a 4-way handshake.
This handshake derives a Pairwise Transient Key (PTK) from the Pairwise Master Key (PMK), which is then used for encryption. To ensure the PTK is unique for every client, two random values are introduced:
SNonce (Supplicant Nonce): A random number generated by the client.
ANonce (Authenticator Nonce): A random number generated by the AP.
For WPA2-PSK, the PMK is the PSK itself, making it relatively easy to reverse-engineer the encryption if the PSK is known. WPA2/3-Enterprise adds an EAP exchange before the 4-way handshake to generate a Master Session Key (MSK), which is then used to create the PMK.
To secure broadcast and multicast traffic within the BSS, a Group Temporal Key (GTK) is used. The GTK is derived from the Group Master Key (GMK), which is held by the AP and distributed to all associated clients.
4-Way Handshake
Let’s break down the handshake as seen in the diagram below:
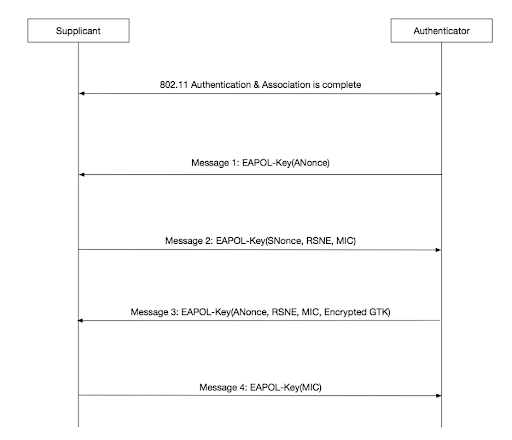
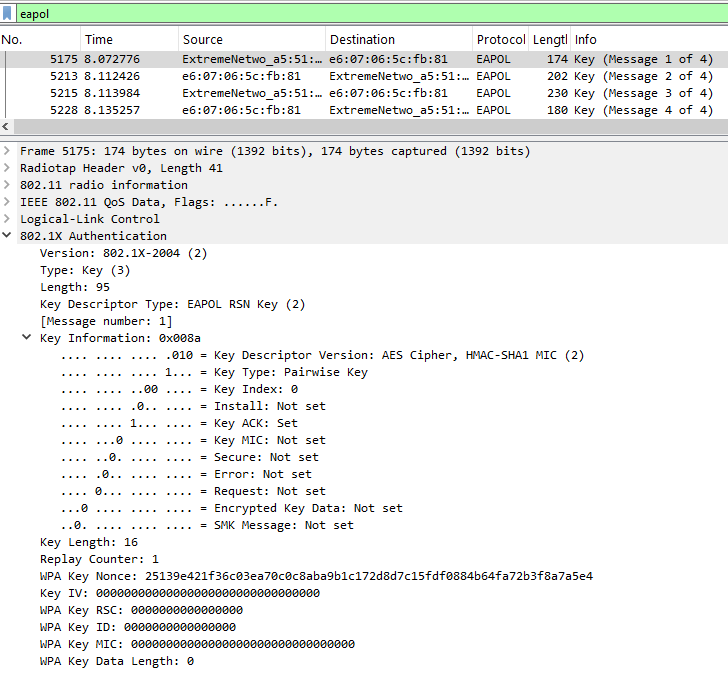
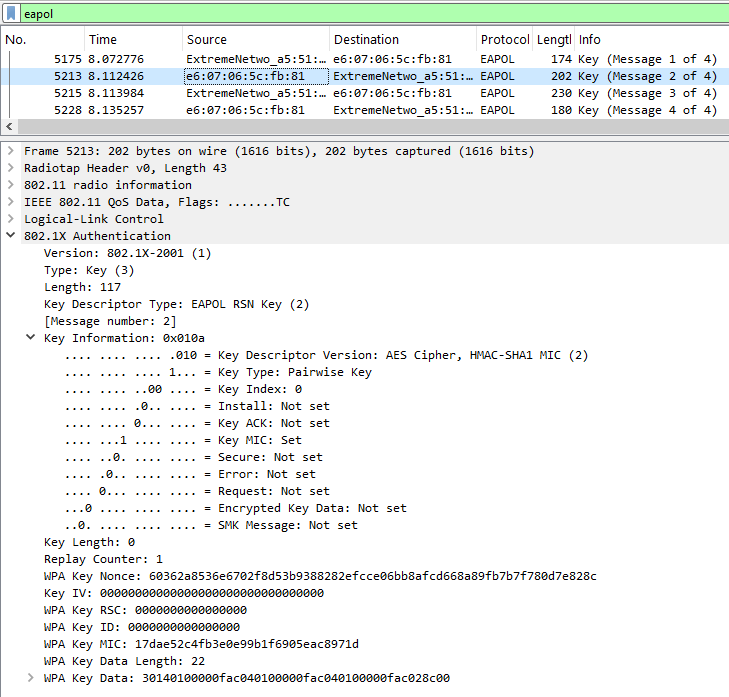
Message 1: The AP (authenticator) sends an EAPOL-Key frame to the client (supplicant), including an ANonce for PTK generation. This frame also specifies the encryption type (e.g., AES Cipher or AES-128-CMAC).
Message 2: The client replies with an EAPOL-Key frame containing an SNonce, RSNE, and MIC (Message Integrity Check). At this stage, the PTK is derived from the SNonce and ANonce. If the PSK is incorrect, the handshake stops here.
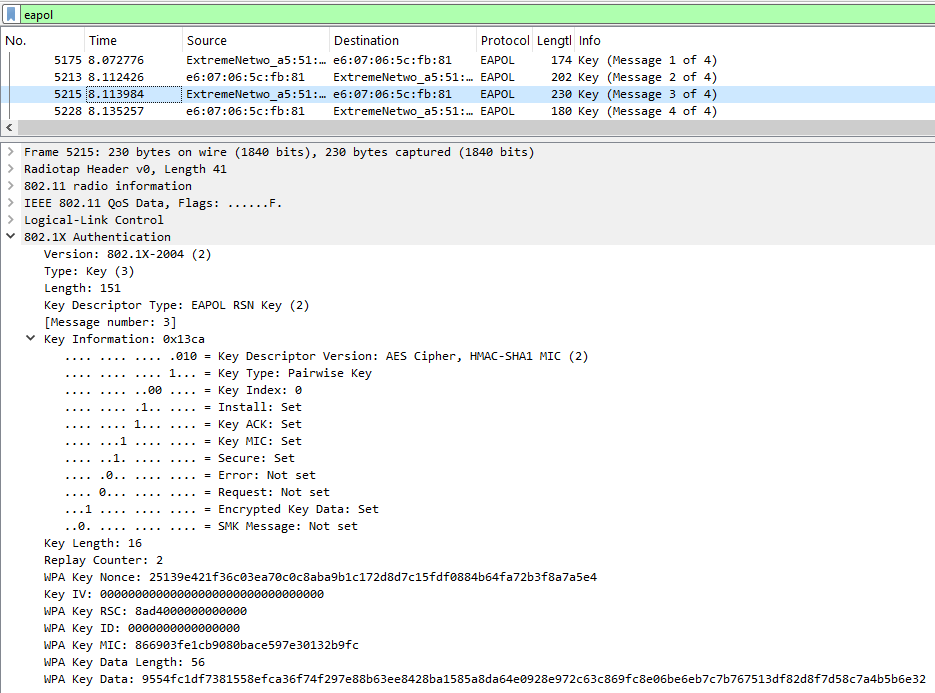
Message 3: The AP derives the PTK and verifies the MIC from the client’s response. It then sends the ANonce, RSNE, MIC, and encrypted GTK back to the client.
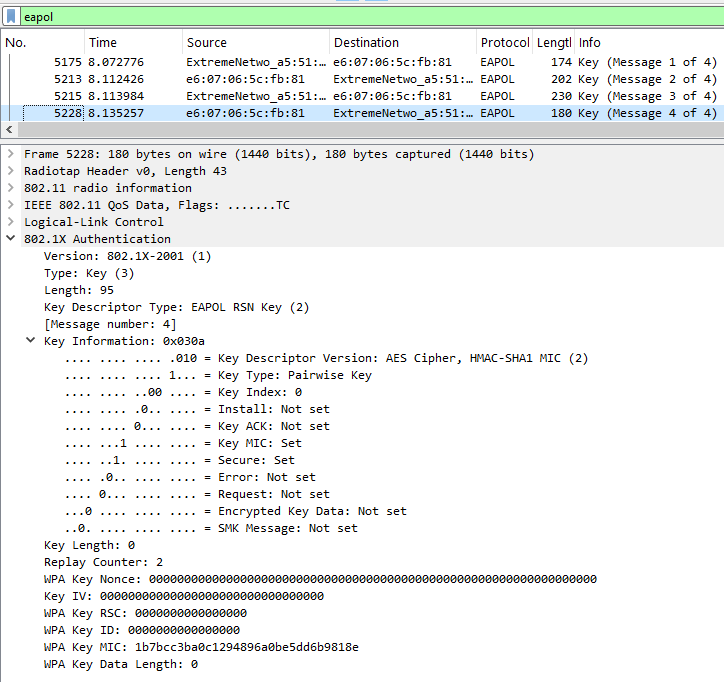
Message 4: The client notifies the AP that the temporal keys have been installed, along with another MIC.
Simultaneous Authentication of Equals (SAE)
WPA3-Personal introduces a new type of encryption called Simultaneous Authentication of Equals (SAE). While it may seem new, SAE was actually introduced earlier in 802.11s for Mesh BSS operations.
In WPA2-Personal, the passphrase serves as the PMK (Pairwise Master Key), which posed a significant risk if the password were leaked. Solutions like PPSK (Private Pre-Shared Key) were introduced to mitigate this risk. SAE is a major improvement because the PMK is unique to each device, and the password is never transmitted over the air.
Instead of directly exchanging the password, a hashed value of the shared password (called the Password Element) is combined with a random number (Nonce) and sent to the other device. Both devices execute this process, which is known as the Commit step. Both devices set the sequence number to 1. The device can derive the Nonce of the other device because it can reverse the Password Element (as it already knows it). In this way, each device can generate a PMK based on both Nonces. In Sequence 2, a Confirm message is sent to the other device to indicate that the PMK was successfully generated. However, you cannot be completely sure that it was successful until after the 4-way handshake.
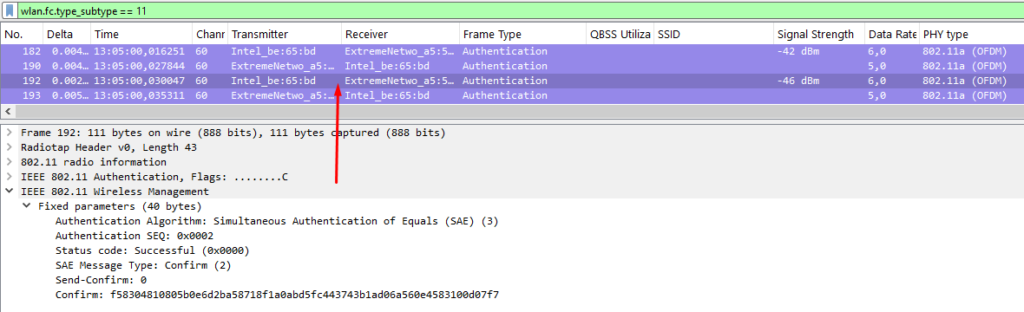
802.11 Roaming
When an access point is part of an Extended Service Set (ESS) and the signal degrades, the station is allowed to reassociate with a new AP. This process is known as roaming. The station decides which metrics will influence the roaming decision, such as RSSI (Received Signal Strength Indicator) and SNR (Signal-to-Noise Ratio).
During roaming, the station exchanges authentication, reassociation frames, possible EAP packets, and completes a 4-way handshake. The reassociation request frame contains information about the currently associated AP, and within the RSN Element you can find the PMKID of the current connection.
Roaming in a WPA2-Personal ESS is relatively fast because the process of obtaining the PMK and generating the PTK is quick. However, with WPA3-Personal (SAE) and WPA2/3-Enterprise, the process takes longer due to the extended PMK generation. This added delay can cause issues, particularly for real-time applications like voice and video calls. Without optimizations, this delay can become noticeable, especially during activities like video conferencing or voice calls.
Fortunately, there are methods to improve roaming performance and reduce roaming time.
Preauthentication and PMK Caching
- Preauthentication: The station can have multiple PMK Security Associations (PMKSA) with other APs. 802.1X authentication against target APs is established via the currently connected AP, resulting in a PMKSA. This eliminates the need to go through the EAP authentication process, leading to faster and shorter connections.
- PMK Caching: The PMK used by the station is cached on the AP. This means that if the station roams back to the same AP and the PMK is still cached (and hasn’t expired), the EAP authentication process does not need to be repeated. However, this caching only works if the station returns to an AP it’s already associated with. It will not work with a previously unassociated AP.
Both legacy methods of Preauthentication and PMK Caching do not scale well in large Wi-Fi deployments. For them to work effectively, every AP must maintain a PMKSA with all associated stations.
Fast Transition
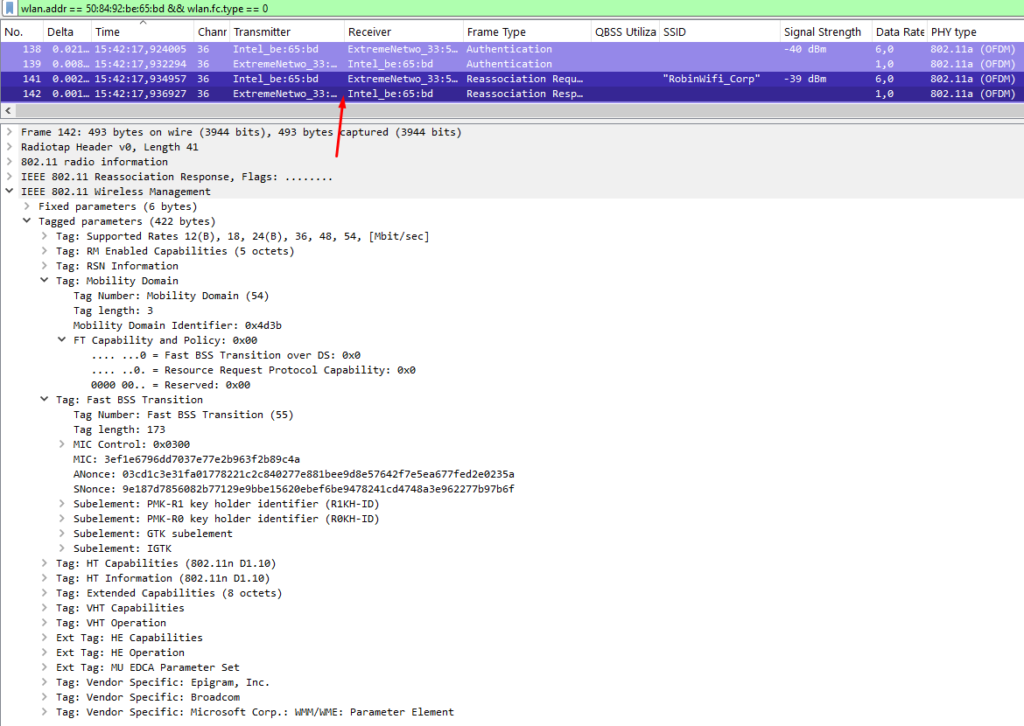
In 2009, the 802.11r amendment introduced Fast (BSS) Transition (FT), revolutionizing Wi-Fi roaming. For stations and APs to participate in this process, they must belong to the same Mobility Domain—an identifier that essentially defines a “roaming domain.” Think of it as a way to group APs together to enable fast and seamless transitions between them. However, it’s best practice to create separate mobility domains for different campuses. This approach minimizes overhead (since APs within a mobility domain communicate with each other) and simplifies troubleshooting by keeping roaming boundaries manageable.
There are two ways that FT can happen: Over-the-Air and Over-the-DS.
Over-the-Air is the common mode you’ll encounter in the field. Both modes speak for themselves. In this mode, a station performs an authentication and reassociation exchange over-the-air and “off-channel” with the target AP. The authentication algorithm is set to Fast BSS Transition (2), and a new PMK is derived from the current AP. Only after this is done does the station disassociate from the current AP and reassociate with the target AP.
Over-the-DS shares some similarities, but instead of sending authentication frames directly to the target AP, it sends FT Action frames to the current AP. The current AP then forwards the frames to possible target APs over the wired network, and the FT Action response is sent back to the station. Once the station receives its desired response, it can dissociate and reassociate with the target AP.
802.11k Neighbour Reports help improve FT by limiting the channels a station should scan to detect target APs. Although this is interesting, I’m not going to dig deeper into this topic for now (as it’s outside the scope of CWAP).
Below you can find an example exchange over-the-air. I wasn’t able to capture the disassociation frames due to my limited setup, but the authentication and reassociation frames are the most important.
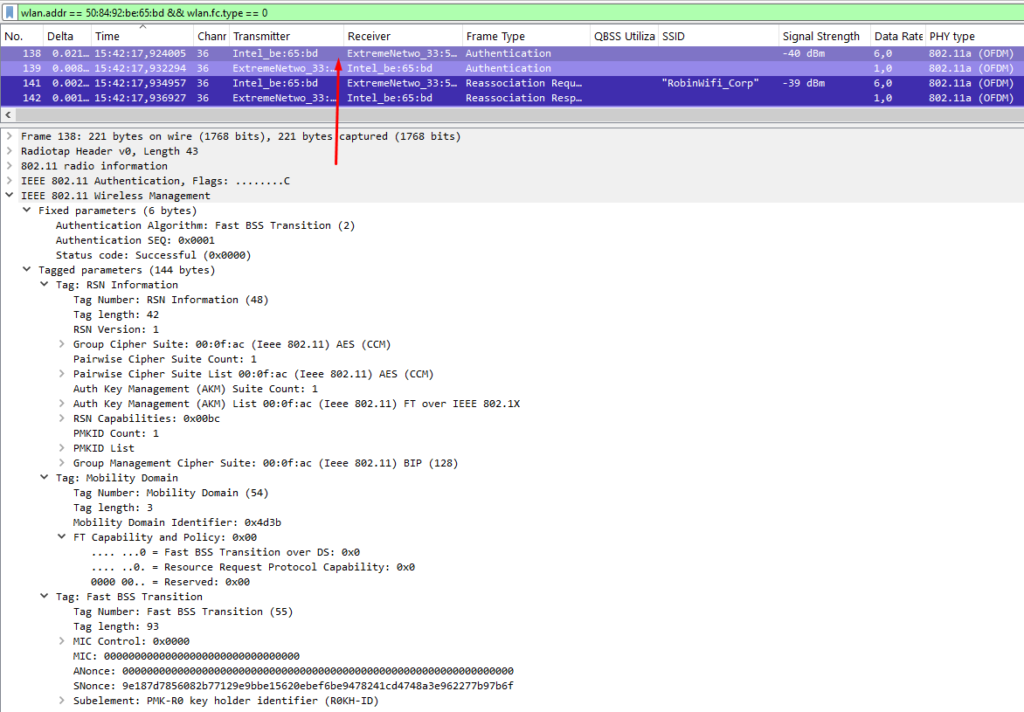
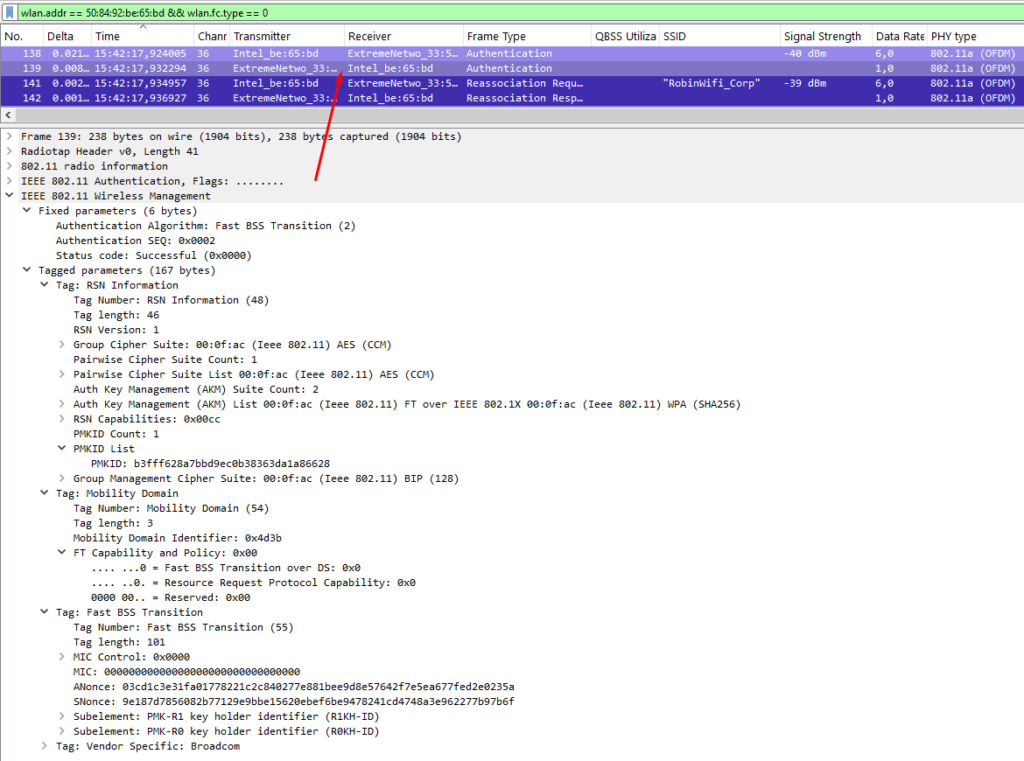
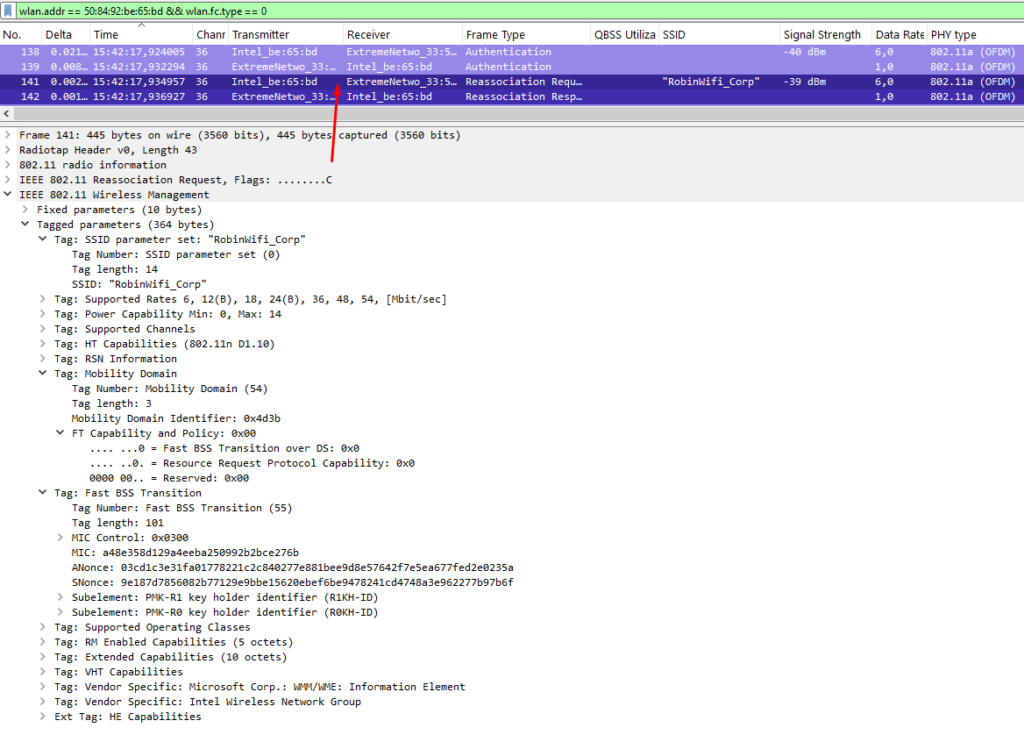
Analyzing and Troubleshooting Roaming Issues
When it comes to roaming issues, there are two main types: clients that don’t roam (sticky clients) and clients that roam too much (excessive roaming).
Because roaming is initiated by the client, it’s sometimes difficult to understand why a client behaves in such a way. One of the major things to look at from the client’s point of view is Layer 1 – PHY support. Does the client allow the channels of neighbouring APs? Does the client maintain an active connection with a distant AP at a low data rate? Perform a wireless capture with your favorite tool (in monitor mode) on the correct channels (remember Chapter 2) and compare the RSSI values from beacon frames to verify whether more suitable APs are nearby for the sticky client. You can reduce “sticky” clients by disabling lower data rates, but this may cause older devices that don’t support higher data rates to drop off the Wi-Fi network.
Excessive roaming is also influenced by the client’s decisions. From my own experience, I’ve found two primary causes for this issue:
- The client is on the edge of the coverage cell between multiple APs, and there isn’t enough overlap. At this point, the client has difficulty choosing between AP1 and AP2, causing it to hop back and forth.
- Default client load-balancing settings are enabled, causing the AP to disassociate clients to encourage roaming.
Cause 1 can be resolved by performing a validation survey and, if necessary, redesigning the coverage areas to allow for a more proportional cell overlap.
Cause 2 can be resolved by disabling the client load-balancing settings. Personally, I’m not a big fan of load balancing through software settings. I prefer to load balance by design—creating small cells with directional antennas in high-density areas. But that’s just my opinion; I’m still learning.
In this chapter, we’ve covered the essentials of 802.11 association, roaming, and security exchanges, from the initial probe requests to the complexities of WPA3’s SAE and roaming optimizations. Understanding the sequence of these frames and how roaming, security, and fast transitions work is key to troubleshooting and optimizing Wi-Fi networks.
Thank you for reading the fifth episode of my CWAP series! I hope you found the information helpful. Stay tuned for the next post, and as always, feel free to leave your thoughts and feedback in the comments below. I’m looking forward to hear from you!
Source(s):
Carpenter, T., et al. (2021). CWAP-404: Certified Wireless Analysis Professional Study Guide (2nd ed.). Durham NC, USA: Certitrek Publishing
You’re blogs are awesome and spot on. I really appreciate the summary.