Chapter 1 gave us a good idea of the direction and objectives in this study guide. This chapter touches on some of those subjects and elaborates more on the specifics.
If we take a step back and think about the first step in WLAN, it starts with locating and discovering Wi-Fi networks. This is also the first challenge in Wi-Fi security. It has been covered in CWNA and CWAP, but it also plays a crucial role in CWSP.
Passive Discovery
Passive scanning is the first and most common method. A station listens during a certain interval (dwell time) on each of its supported channels for beacon frames. If a beacon frame with a particular SSID is seen and recognized, the station can either connect manually or automatically.
Since beacon frames are rich in information, they also reveal the security mechanisms configured on the network. A WPA-certified device will show a WPA Information Element (IE). With WPA2, we can find security type information in an RSNE (Robust Security Network Element) information field.
Although WPA is no longer used, you may very rarely encounter it in the form of an old AP transmitting in some compatibility mode, enabling both WPA and WPA2. In this case, both the WPA and RSNE IEs are present in beacon frames.
Attackers are mainly interested in these beacon frame information elements:
- Capability Information Elements
- SSID
- Supported Rates
- RSNE
Active Discovery
Active discovery is the second method for locating APs. This works by a station sending probe requests (with an SSID element) on each of its supported channels and waiting for probe responses. The Destination Address in these probe requests is a broadcast address, as no specific AP has been identified yet.
The SSID element in probe requests can either contain a list of preferred SSIDs or a wildcard/broadcast value (*). If set to a wildcard, any AP that hears the transmission can respond with its own SSID.
A significant privacy risk associated with active WLAN discovery is the potential for a mobile device to send probe requests for specific SSIDs, such as “SOMECORP.” This can inadvertently reveal information about the user’s current or past connections, such as their employer.
Imagine someone with malicious intentions sitting in a coffee shop, waiting for people to come in and order their coffee. With the right tools and filters, they can capture these probe requests and easily identify potential targets based on the SSIDs being probed. This makes it a great place for gathering information on individuals and their affiliations.
Although the 802.11-2020 standard requires APs to respond to wildcard/broadcast SSID probe requests, some manufacturers allow administrators to disable this response. This reduces the risk of being discovered in wardriving scenarios, where an attacker moves through an area (e.g., a shopping mall) while broadcasting probe requests to collect data for further analysis.
Wardriving is often combined with location tracking (GPS) so attackers can log the exact location where a particular weak SSID was detected.
6 GHz Discovery Methods
802.11ax and 6 GHz introduced new options for Wi-Fi discovery. One of them is “out-of-band discovery.”
Since 6 GHz adds many more channels, scanning all of them takes significantly more time. If your SSID is broadcast on multiple bands, a device is more likely to detect a 2.4 GHz or 5 GHz beacon first before discovering the same SSID in 6 GHz.
To improve 6 GHz discovery, a Reduced Neighbor Report (RNR) element can be included in beacon frames and probe responses in the lower bands. Based on the 802.11v amendment, this feature allows an AP to advertise its presence on 6 GHz, as well as nearby 6 GHz APs, speeding up the discovery process.
In-band discovery works similarly to traditional passive and active scanning on 2.4 GHz and 5 GHz. However, active scanning is limited and discouraged in 6 GHz. This is managed through Preferred Scanning Channels (PSC). With significantly more spectrum available (though the EU is still trailing behind the US in fully opening it up), 80 MHz channel widths are expected to become standard. Because of this, it’s generally unnecessary to actively probe every 20 MHz channel.
PSC channels act as designated scanning points within 80 MHz-wide channels, allowing clients to find networks more efficiently. To further reduce probe request overhead—especially in high-density environments—clients must wait at least 20 time units before sending probe requests. This delay provides enough time to passively detect beacons or receive unsolicited probe responses.
Passive discovery is the third method used for 6 GHz discovery. In addition to beacons and probe responses, clients can also listen for FILS Discovery Announcement frames. FILS (Fast Initial Link Setup) is a set of mechanisms designed to optimize discovery, authentication, and higher-layer setup, but I won’t dive into those details just yet.
Security by Obscurity: SSID Hiding and MAC Filtering
Now that we’ve discussed discovery methods and their risks, let’s address features that pretend to be security measures but really aren’t.
Two commonly misunderstood security features are SSID Hiding and MAC Filtering.
SSID hiding is a setting that prevents the SSID from being included in beacon frames. However, it is not a real security measure because the SSID still appears in probe responses, (re)association frames, and probe requests from client devices. This means that attackers can still easily discover the SSID using tools that monitor active discovery frames. Hiding an SSID is only useful in limiting guest access, but it can actually cause connection issues for legitimate corporate devices.
A similar misconception applies to MAC filtering. While it allows administrators to create an “allowed list” of devices that can connect to the AP, it is not a real security feature because MAC spoofing is trivial. Changing a MAC address can be done using built-in OS tools or third-party software. If an attacker captures a frame from a legitimate connected device, they can easily clone that MAC address and bypass filtering. Because of this, MAC filtering is not a security feature—it’s just a way to prevent casual users from connecting.
EAP: Some Defend, Some Pretend
In Chapter 1, I already talked about WEP and shared key authentication, which should not be used in today’s Wi-Fi networks. A PSK (Pre-Shared Key) comes with the risk of being leaked, allowing unauthorized access to the network. However, that doesn’t mean EAP (Extensible Authentication Protocol) is completely risk-free.
Two EAP methods that are highly vulnerable and must be avoided are EAP-MD5 and Cisco’s LEAP.
EAP-MD5 does not provide dynamic encryption key management, mutual authentication, or any real security features. (Carpenter et al., p. 77) Since it only performs a simple one-way hash of the user’s credentials, it’s vulnerable to offline dictionary attacks.
LEAP, on the other hand, was an early attempt to improve security after WEP but before 802.11i (CCMP/AES) was ratified. Initially, it was limited to Cisco devices (both clients and APs), though support was later extended to non-Cisco devices through Cisco Compatible Extensions (CCX).
The main vulnerability with LEAP was that usernames were transmitted in clear text, and no tunneling mechanism was used to protect authentication. This made it vulnerable to offline dictionary attacks—attackers could capture authentication traffic and crack passwords due to LEAP’s reliance on a weak MS-CHAPv2-based authentication mechanism.
The recommended EAP method is EAP-TLS (certificate-based), but it comes with the overhead of deploying a PKI. Another widely used option is EAP-PEAP (username + password), though it’s inherently vulnerable to credential theft. There’s definitely more to cover on EAP in the upcoming chapters.
Denial-of-Service (DoS) Attacks in Wi-Fi
DoS attacks were already covered in the previous chapter and remain one of the biggest challenges in Wi-Fi today. We can break them down into Layer 1 (RF-based) DoS and Layer 2 (MAC-based) DoS.
Layer 1 (RF) DoS Attacks
RF DoS can be intentional or unintentional.
- Unintentional RF DoS happens due to accidental RF interference from microwave ovens, cordless phones, baby monitors, wireless cameras, or even a neighbor’s poorly configured Wi-Fi network.
- Intentional RF DoS is a targeted attack known as RF Jamming. As the name suggests, it works by continuously transmitting and occupying the RF spectrum—either narrowband or wideband—effectively disrupting communication.
This type of attack is illegal, but detecting and stopping it can be tricky.
- Narrowband jamming can sometimes be mitigated by APs switching channels through RRM (Radio Resource Management).
- Wideband jamming requires WIDS/WIPS to detect it, though ultimately, physical security measures are needed to locate and remove the jammer.
The only ‘good’ thing about RF jamming is that it’s typically localized, meaning it won’t take down an entire hospital’s Wi-Fi network, for example.
Layer 2 (MAC) DoS Attacks
Layer 2 DoS attacks typically involve disassociation or deauthentication frames.
A common example is the deauthentication attack, where an attacker spoofs deauthentication frames, pretending to be the AP. When a client receives these frames, it disconnects from the Wi-Fi and either attempts to reconnect or stays offline.
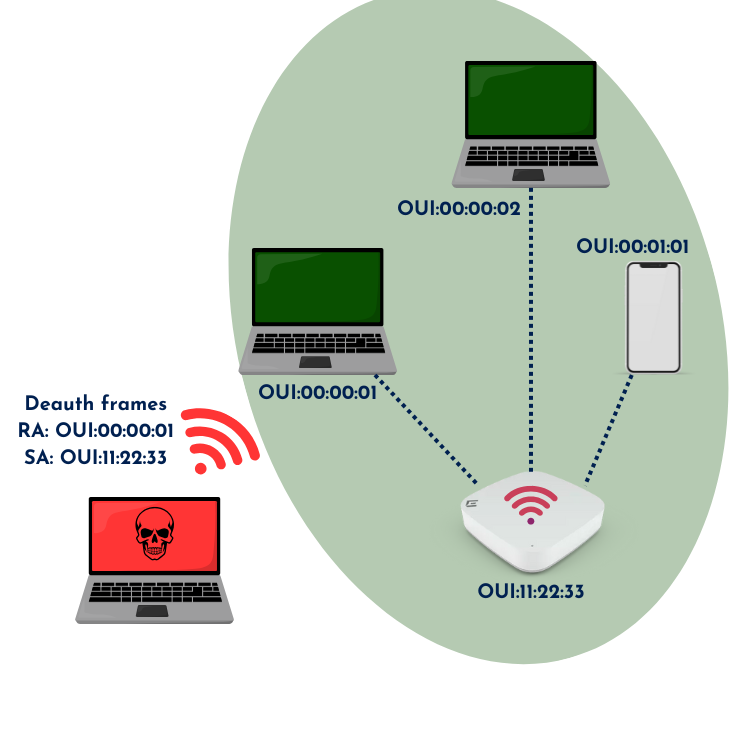
The goals of such an attack can vary:
- Disrupt communication by repeatedly disconnecting all clients
- Capture a 4-way handshake for cracking WPA2-PSK
- Trick a client into connecting to a rogue AP
A rogue AP can act as a Man-in-the-Middle (MitM), capturing unencrypted client traffic and forwarding it to a legitimate AP or switch. This way, the client doesn’t even realize something is wrong. A MitM attack could also trick users into entering login credentials through a fake captive portal page.
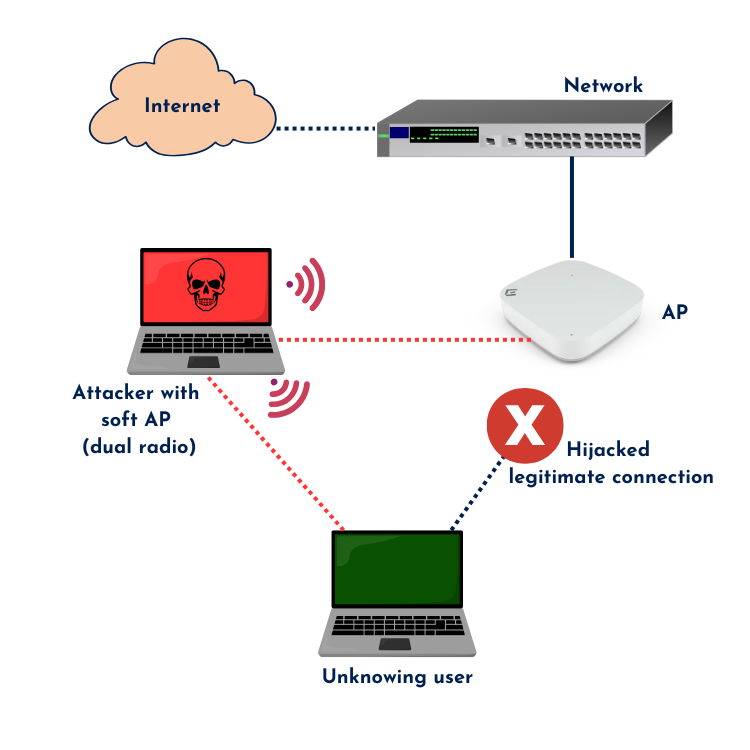
Management Frame Protection
Fortunately, 802.11w (Management Frame Protection) helps mitigate this by encrypting management frames. With MFP enabled, clients will ignore unauthenticated deauthentication frames and only trust encrypted communications from the AP. However, there’s a downside—some legacy devices don’t support 802.11w, which may prevent them from connecting to the network. Note that when using WPA3, it is required to use MFP by the 802.11-2020 standard. I don’t think there is even an option to turn on WPA3 with 802.11w disabled.
Additionally, MFP does not prevent users from manually connecting to a rogue AP. That’s where stronger authentication methods, such as EAP-TLS, come into play. A PSK can still be cracked or leaked, making certificate-based authentication the better alternative.
Authentication Vulnerabilities
Here’s a quick rundown of vulnerable authentication methods that should be avoided:
- 802.11 Shared Key Authentication → The challenge hash is easily recovered (clear-text challenge + encryption key), exposing the WEP key.
- EAP-MD5 → Lacks dynamic encryption key management or mutual authentication—capturing a few frames allows attackers to crack the MD5 hash.
- LEAP → Usernames are transmitted in plain text, and tools like ASLEAP can crack weak passwords through dictionary attacks.
- WPA-Personal & WPA2-Personal → Weak passphrases can be brute-forced after capturing a 4-way handshake. Since 2017, we’ve had to deal with KRACK—an attack that exploits the 4-way handshake process, targeting both authentication and encryption.
Is WPA2-Personal secure?
When it comes to encryption cracking, it should be clear by now that WEP and TKIP/RC4 should be completely avoided. CCMP/AES is considered uncrackable and is highly recommended. However, that doesn’t mean WPA2-Personal is invulnerable. In my CWAP Chapter 5 blog post, I already covered how the 4-way handshake works and how traffic can be decrypted if the PSK is known. Even without knowing the PSK, it is now possible to crack and decrypt WPA2-Personal AND Enterprise using the KRACK vulnerability.
KRACK works by forcing key reinstallation—repeatedly sending the third message of the handshake to gradually decrypt traffic. For more details on KRACK, check out this reference.
Physical Security and Public Access Networks
Other common concerns include physical security and public access networks.
Physical security is just as important as digital security—not only to prevent APs from being taken offline but also to stop rogue APs from being placed on unsecured Ethernet ports.
Public Access Networks, such as guest Wi-Fi, are often unsecured, posing a major risk to users. A key consideration for guest networks—whether secured with a PSK or not—is peer-to-peer communication (also called client-to-client traffic). Many consumer-grade APs don’t support the ability to block this type of traffic, leaving clients vulnerable to direct attacks from other users on the same network.
Best practice is to completely isolate guests from the rest of the network and only allow internet access. You may also want to restrict network traffic by allowing only secure protocols like HTTPS and secure email ports via AP firewall rules to minimize damage if the network is compromised.
General Recommended Practices
To conclude this chapter, the CWSP advises on some general recommended practices:
- Use the latest security suite whenever possible (minimum WPA2)
- Replace legacy solutions and clients with modern ones
- Upgrade firmware when appropriate
- Implement Lifecycle Management Procedures for WLAN security
(Carpenter et al., p 101)
Wi-Fi security is more than just encryption; it involves securing every layer of the network to prevent unauthorized access, data theft, and denial-of-service attacks. From weak authentication or encryption methods like EAP-MD5 and WEP to RF jamming and Layer 2 deauthentication attacks, there are many vulnerabilities that attackers can exploit. Thankfully, strong encryption, proper authentication methods, and management frame protection can significantly enhance security. However, no single security measure gives you full protection, and continuous monitoring, updates, and best practices are essential. If you’re securing a wireless network, always remember: encryption alone isn’t enough—layered security is key.
Source(s):
Carpenter, T., et al. (2023). CWSP-207: Certified Wireless Security Professional Study Guide (1st ed.). Durham NC, USA: Certitrek Publishing