Security policies are crucial in any environment, but especially in wireless networking. These policies provide a structured framework for handling security incidents and implementing protective measures. A well-documented security policy defines minimum security requirements and outlines how access is granted or denied. This chapter focuses on why security policies are necessary and how they can be effectively implemented.
CWNP defines a policy as a documented set of operational parameters in the form of a management-endorsed agreement. It includes rules, regulations, and courses of action for different situations based on an organization’s needs.
When extended to security, this becomes a security policy. However, there is no universal security policy that fits every organization. While best practices exist, they can vary by vendor, as some have proprietary tools or protocols. Policies should also evolve as an organization changes—for example, when new IoT systems are deployed.
Regulatory Compliance and Legal Considerations
A major aspect of a security policy is ensuring compliance with the IEEE 802.11 standard and regulatory agencies such as:
- FCC (US Tx Power, frequency regulations, etc.)
- ETSI (Europe Tx Power, frequency regulations, etc.)
- HIPAA (US healthcare data protection)
- GDPR (EU personal data protection)
Failing to comply with these regulations can lead to legal consequences. The organization’s legal team should be involved in security incidents, as forensic analysis may be needed for evidence. If a data breach or significant damage occurs, local authorities must be alerted. It’s one of the reasons why job descriptions like ‘Data Protection Officer’ exist.
Why Is a Security Policy Important?
The key drivers for establishing a security policy include:
- Maintaining the desired level of network security
- Ensuring regulatory compliance
- Providing legal protection
- Documenting organizational assets
- Ensuring procedural continuity
- Defining authority and responsibility
(Carpenter et al., p.112)
However, just having a policy isn’t enough—it needs to be well-maintained. Continuous monitoring is just as important as the policy itself. If an organization fails to enforce it, the policy might as well not exist. Even small inconsistencies can be security gaps.
For example, allowing personal devices like smartphones or smartwatches to connect to a corporate SSID could violate security policies. BYOD devices should typically be restricted to guest networks—perhaps without the need for a captive portal, but still segmented from critical resources.
Using the same password everywhere might feel convenient, but so would using the same PIN to unlock your phone and pay with your credit card. If someone sees you enter it once, they now have access to both. The same goes for passwords—if you use the same one for your local store’s webshop and your corporate login, a single breach can compromise far more than you think.
As Phil Morgan wisely says:
“Inconvenience is a hacker’s best friend.”
This phrase couldn’t be more accurate. Hackers thrive on weak or non-existent security practices. If you’re unwilling to add even a little inconvenience to your routine—whether it’s using strong, unique passwords or enabling multi-factor authentication—you’re making it far more convenient for an attacker to gain access. A small hassle for you can mean a massive roadblock for them.
Steps for Implementing a Wireless Security Policy
To create and enforce a wireless security policy, consider the following steps:
- Perform a risk assessment.
- Define and document vulnerabilities and countermeasures.
- Obtain support from senior management.
- Provide communications between the involved parties.
- Provide ongoing monitoring and support.
- Plan response, forensics, enforcement, and reporting tactics in advance of a security policy breach.
- Identify key security team players for policy breach situations.
- Revise and fine-tune the policy as needed.
- Publish all changes to the security policy and provide an educational forum to keep users apprised of current status.
(Carpenter et al., p.114)
A security policy is not just one person’s responsibility —it requires collaboration across multiple departments, including management, IT security, legal teams, and physical security staff.
Risk Assessment and Security Audits
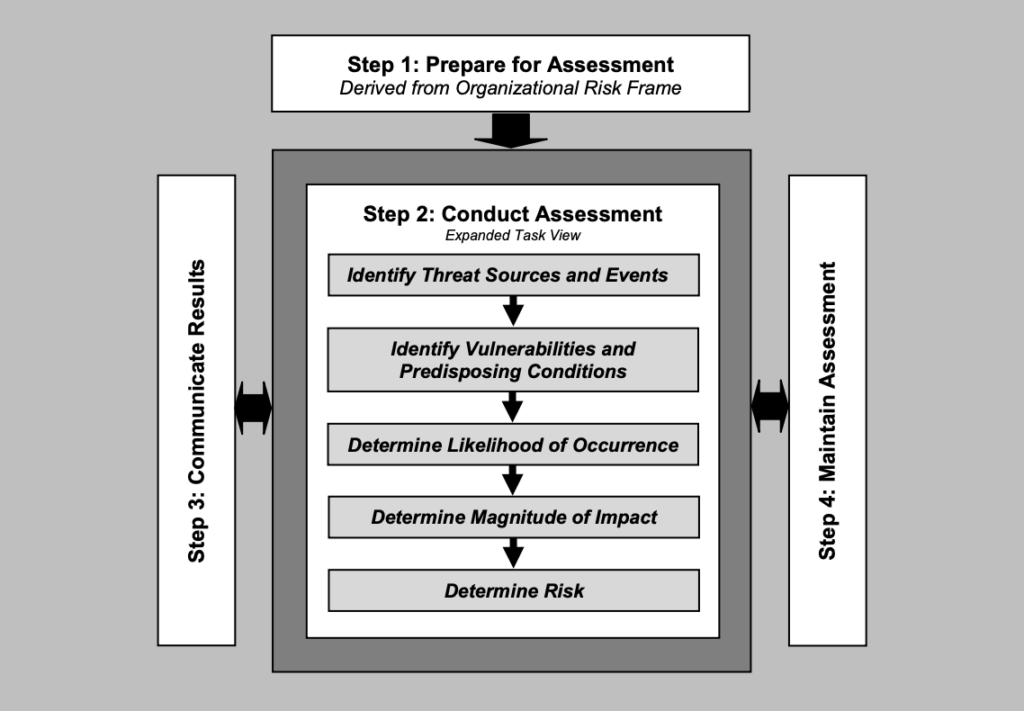
Performing a risk assessment is a critical first step where risk can be explained as the likelihood and impact of the realization of a threat. It is some kind of function between the likelihood of occurrence vs the impact or damage a threat may cause. This risk assessment process is basically a security audit and has some steps outlined for you to follow. These are the core steps for performing a risk assessment according to the US National Institute of Standards and Technology (NIST) Special Publication 800-30 (nist.gov, 2012):
- Identify threat sources and events
- Identify vulnerabilities and predisposing conditions
- Determine likelihood of occurrence
- Determine magnitude of impact
- Determine overall risk
Measuring and Prioritizing Risks
Identifying risks is just one part of the equation—measuring risk is equally important. Some risks naturally take higher priority than others. The loss expectancy metric helps quantify risk by estimating the potential financial impact of a security incident (e.g., customer data theft).
To calculate risk in financial terms, we use the following formula:
Single Loss Expectancy (SLE) × Annual Rate of Occurrence (ARO) = Annualized Loss Expectancy (ALE).
ALE helps determine which risks require immediate attention. However, risk isn’t just about financial loss—it also affects an organization’s reputation, regulatory standing, and operational stability.
After conducting a risk assessment, document the risks along with their possible countermeasures. Keeping this documentation up to date and accessible to all stakeholders is essential.
One of the most critical steps is securing management buy-in. No matter how skilled you are, you can’t mitigate risks alone. Management needs to be involved—not only because loss expectancy values are difficult to calculate without business insights, but also because security measures require funding. Naturally, that budget has to be justified with solid risk assessments.
Incident Response Planning
Once risks have been identified, the next step is to prepare for the inevitable—because at some point, a security incident will happen. Having a clear incident response plan in place ensures that when things go wrong, you’re not scrambling to figure out what to do.
Ask yourself:
- What’s the immediate response if a rogue AP is detected?
- How do you handle a lost or stolen laptop or AP?
- Who needs to be informed in the event of a security breach?
- What’s the backup strategy for critical assets?
A strong incident response plan should cover a variety of security scenarios with clearly defined actions. Flowcharts can be great for visualizing the response process, but depending on the complexity of the situation, detailed written guidelines may be necessary. The key is to ensure that everyone involved—IT, security teams, and even management—knows their role when an incident occurs. Reacting quickly and effectively can mean the difference between a minor inconvenience and a full-scale security disaster.
Security Policies Beyond Configuration
Simply following best practices for security configurations isn’t enough—strong policies must be in place to govern how users interact with the network and what security measures they must follow. Even the most secure setup can be compromised by human error or negligence, so enforcing these policies is just as important as configuring firewalls and encryption.
Key security policies include:
- Password Policy – Enforcing strong passwords, expiration rules, and multi-factor authentication (MFA) to prevent unauthorized access.
- Acceptable Use Policy – Defining what users can and cannot do on the network to minimize security risks.
- Security Awareness Training – Educating employees on social engineering, phishing, and other common attack methods to reduce the risk of human-related breaches.
- Bring-Your-Own-Device (BYOD) Policy – Ensuring that unmanaged personal devices don’t have unrestricted access to corporate resources.
- Endpoint Security – Requiring antivirus software, firewall agents, and device posture checks to keep devices compliant and protected.
- Social Media Policy – Blocking or restricting access to high-risk platforms that could lead to data leaks or malware infections.
Depending on the organization, additional policies—such as strict firewall rules for guest networks or geofencing to prevent access from unauthorized locations—may also be necessary. Security isn’t just about the technology—it’s about the rules that govern how it’s used.
Security Audits and Penetration Testing
Regular security audits are critical for ensuring that configurations remain up-to-date, security measures are properly implemented, and potential vulnerabilities are identified before they become actual threats. Security isn’t a one-and-done deal—it requires continuous evaluation to stay ahead of evolving risks.
In regulated industries, an external audit may not just be a good practice but a strict requirement. These third-party auditors conduct thorough assessments to validate compliance and security effectiveness. One of the most valuable aspects of these audits is penetration testing (pentesting), where real-world attack scenarios are simulated to uncover weaknesses that could be exploited by malicious actors.
These pentests can include:
- Authentication cracking
- Deploying rogue devices
- Social engineering attacks (e.g., impersonating an employee)
Continuous Monitoring with WIDS/WIPS
One of the most effective defenses against evolving security threats is continuous monitoring and alerting. Modern Wireless Intrusion Detection Systems (WIDS) and Wireless Intrusion Prevention Systems (WIPS) provide automated security monitoring by detecting anomalies and suspicious behavior.
When a potential threat is detected, the system can alert administrators and even take automated actions—such as blocking unauthorized access. Automation enables real-time threat response without manual intervention, significantly improving security efficiency.
Of course, false positives can occur, but proper tuning minimizes unnecessary alerts while ensuring legitimate security risks are addressed. And in some cases, an alert might just mean that someone in your organization is doing something they shouldn’t be.
Defining Wi-Fi Security Policies
A well-defined Wi-Fi security policy is more than just a set of rules—it’s a foundation for protecting your network from threats while ensuring smooth operations. CWNP outlines key elements that should be included in any strong security policy to maintain control, visibility, and compliance. These elements cover everything from authentication and encryption to device management and network segmentation. Here’s what a comprehensive Wi-Fi security policy should address:
- SSID Naming (clear and standardized naming conventions)
- Authentication Mechanisms (PSK, 802.1X, Captive Portal, etc.)
- Supported Encryption Types
- Allowed Device Types (e.g., Dell laptops, Zebra scanners, HP printers)
- Device Labeling & Naming Conventions
- Rogue AP and Client Policies (WIDS, WIPS enforcement)
- Endpoint Security Requirements (password policies, certificates, etc.)
- Default Configuration Baselines
- Remote Networking Policies (VPN usage guidelines)
- Management Protocol Security (e.g., enforcing SSH over Telnet)
- Monitoring & Logging (Syslog, SIEM, WIPS/WIDS integration)
- Network Segmentation (VLAN policies)
- Role-Based Access Control (RBAC) (802.1X authentication strategies)
(Carpenter et al., p127-128)
Okay, that was a lot of lists. But creating a security policy isn’t just about ticking boxes—it’s about asking the right questions and making sure you’ve covered all the bases. Security isn’t a one-time setup; it’s an ongoing process that needs regular updates, monitoring, and sometimes a bit of troubleshooting when things don’t go as planned.
A well-structured policy gives you a solid foundation to keep your Wi-Fi network secure, compliant, and running smoothly. It helps prevent security gaps, ensures everyone follows the same rules, and makes responding to incidents way easier. If you haven’t thought about some of the things mentioned here, now’s the time to take a closer look.
And if you have? Well, give yourself a pat on the back—but don’t get too comfortable. Security is always evolving, and there’s always something new to learn.
Source(s):
Carpenter, T., et al. (2023). CWSP-207: Certified Wireless Security Professional Study Guide (1st ed.). Durham NC, USA: Certitrek Publishing
Nist.gov. (2012) NIST SP 800-30. Retrieved February 14, 2025, from https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
Good write up.