Kicking off my CWNE journey with Chapter 1, which lays the groundwork for wireless security. If you’ve been following my CWAP posts, you know I’m all about the technical deep dives, but security is a whole different beast. This chapter covers everything from the fundamental principles of securing a WLAN to the threats that lurk in the airwaves and on the wired side of things. It’s not just about encryption and authentication—it’s about understanding how security fits into every layer of the OSI model.
What the WEP?
The foundation of security in any system is based on the CIA triad—Confidentiality, Integrity, and Availability. Back in the day, WEP (Wired Equivalent Privacy) was introduced to secure WLANs, but it had a pretty basic goal: just prevent casual eavesdropping, like intercepting open Wi-Fi traffic without cracking keys. WEP relied on a 24-bit Initialization Vector (IV) combined with a reusable 40-bit or 104-bit encryption key to encrypt data.
The problem with WEP is how it handles these IVs. They’re only 24 bits long, sent in the clear, and reused far too often. After 2^(24) packets, IVs will inevitably repeat—a situation known as a collision, where two or more frames end up encrypted with the same IV and key. This is a massive issue because WEP uses RC4, a stream cipher that’s not designed to reuse the same key stream. When collisions happen, attackers can compare the ciphertexts from the colliding frames to cancel out the key stream and reveal a combination of the original data. This works because of the XOR operation, which is like a logical flip-switch: if you compare two identical values, the result is 0, and if they’re different, the result is 1. Attackers use this property to break WEP encryption, leaving it completely exposed with enough captured traffic.
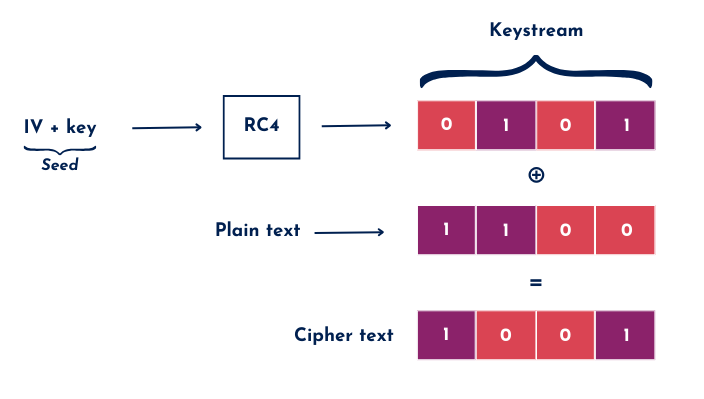
To make things worse, WEP doesn’t automate key changes before IVs are exhausted, so the encryption setup is fundamentally flawed. While it may have stopped casual eavesdropping back in the day, WEP is far from meeting today’s security standards.
Several high-profile hacking incidents made WEP’s lifetime very short and has led to the introduction of Robust Security Network Association (RSNA) in the form of WPA. An RSNA is defined as an association between a pair of STAs which includes a 4-way handshake or uses the Fast Initial Link Setup (FILS) authentication. WEP is now called a pre-RSNA and should of course not be used anymore, and luckily most of the devices have dropped support for it years ago. Because of backwards compatibility, there is a transitional security network (TSN) option, whom can be identified in the RSN Information Element.
Another key aspect of Wi-Fi Security is the fact that RF doesn’t respect boundaries. This is very logical, but should not be overlooked. Although for Wi-Fi to work, both AP and client must hear eachother, but for just capturing traffic (à eavesdropping ) it can be performed at a greater distance than you might expect. That’s just the reality and you can assume that someone with malicious intentions will always find a way to detect and listen to your precious Wi-Fi communications. That is why one should take every other possible measure to secure their Wi-Fi as good as possible, with the most secure methods and algorithms in place.
Cybercrime motives and targets
Why would one want to hijack your Wi-Fi? The primary motive is most always money (or politics). First of all, your own privacy and that of everyone else on the Wi-Fi will be compromised. Personal, medical, financial and login information can be captured, whom can be further exploited. Intruders may insert malware, viruses or backdoors onto your computer or even get access to (corporate) files and servers. The same intruder can also perform illegal activities on your personal network and thus hiding behind your IP and identity. They can disrupt your network devices and/or consume all the bandwidth and result in a Denial-of-Service.
In Large enterprises, the main network targets are Databases, application servers, file servers, management and network infrastructure devices. Most, if not all, are located on the wired network. This is one of the primary reasons why you should use different networks and put a firewall in between the Wi-Fi networks and the wired networks, so you can control the access to your wired resources based on multiple metrics.
Security Concepts review
Let’s review some of the security concepts whom have already been covered in CWNA.
Open System Authentication:
- Utilizes a null authentication algorithm.
- Involves two management frames.
- Essentially, it’s just devices saying, “I want to talk to you” and “I want to talk to you too.”
- Used in WPA/WPA2 and open SSIDs as an authentication method before encryption through the 4-way handshake.
Shared Key Authentication:
- Combines authentication and encryption based on WEP.
- Involves four management frames.
- The challenge string is sent in clear text in the second frame, making it easily exploitable.
Wi-Fi Protected Access (WPA):
- Created by the Wi-Fi Alliance as a temporary security method to bridge the gap between WEP and more robust future security mechanisms.
- Enhances WEP with TKIP to protect data frames.
- WPA-Personal: Allows up to 63 ASCII characters, transformed into a 256-bit PSK using the TKIP/RC4 cipher suite.
- WPA-Enterprise: Uses 802.1X authentication (accept/deny) and encrypts with the same TKIP/RC4 cipher suite.
WPA2:
- Uses the CCMP/AES cipher suite with optional support for TKIP/RC4 for backward compatibility.
- 128-bit encyption key
- WPA2-Enterprise: Supports 802.1X role-based access control based on RADIUS attributes.
WPA3
- Personal Mode: Uses SAE for authentication and encryption.
- Mandatory use of Protected Management Frames.
- Drops support for legacy security protocols like TKIP/RC4.
- WPA3-Enterprise 192-bit mode mandates a minimum security strength of at least 192 bits in all cryptographic functions.
- Uses authenticated encryption based on GCMP-256.
- Key derivation and confirmation using HMAC-SHA384.
- Key establishment and authentication via Elliptic Curve Diffie-Hellman exchange and Elliptic Curve Digital Signature Algorithm (ECDSA) using a 384-bit elliptic curve.
- Provides robust management frame protection built on the 256-bit Broadcast/Multicast Integrity Protocol Galois Message Authentication Code (BIP-GMAC-256).
(Carpenter et al., p17)
Wi-Fi Security Best Practices in Different Environments
Different environments have different needs, but overall it’s about having the right resources (budget, time, people) to implement security best practices as best as you can. Below is an overview on what you can and should do.
Home Office:
- Change all default settings, including SSID, passphrase, and login credentials.
- Avoid using WEP, TKIP, and WPA.
- Ensure all client devices support at least WPA2 and CCMP/AES.
- Use strong passphrases and change them periodically.
- Update your passphrase if you lose a client device.
- Be cautious about sharing your passphrase and monitor family members sharing it with visitors.
- Disable Wi-Fi Protected Setup (WPS) features to prevent vulnerabilities.
- Regularly update devices (clients and routers/APs) to the latest firmware versions.
Small Business:
- Build upon home office best practices.
- Implement stronger authentication mechanisms like 802.1X/EAP (many cloud vendors offer this without needing a physical server on-site, simplifying deployment).
- Educate staff and provide security training.
- Consult outside security experts if your company lacks the necessary expertise to deploy and maintain network security measures.
Large Enterprise:
- Apply all the above rules as a minimum standard.
- Implement port-based and role-based access control through 802.1X/EAP on both wired and wireless networks.
- Prefer EAP-TLS or EAP-TEAP (certificate-based) for EAP methods.
- Use WPA3 if possible, ensuring all clients support it.
Public Networks:
- Use a VPN connection whenever possible.
- Secure all login accounts with strong, unique passwords and use multi-factor authentication (MFA).
- Ensure firewall software is installed, enabled, properly configured, and up to date.
- The same applies to antivirus software.
These are standard best practices. Generally, aim to use the most secure methods like WPA3 and 802.1X where possible, and update passphrases periodically. More advanced techniques, such as Wireless Intrusion Detection and Prevention Systems (WIDS and WIPS), will also be covered in this CWSP study guide.
Wi-Fi Security and the OSI model
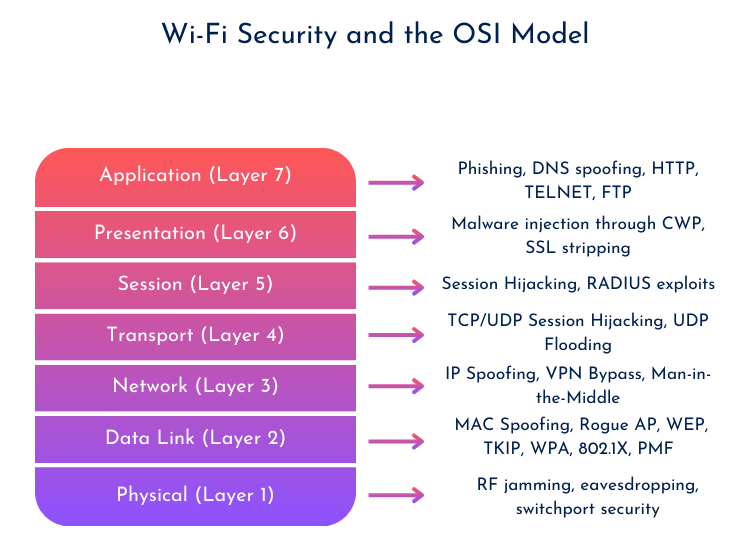
Security concerns exist at all layers of the OSI model, but 802.11 primarily focuses on Layer 1 and Layer 2. Starting with the Physical Layer (L1), the main concerns revolve around RF interference. RF interference can degrade performance or even completely disrupt traffic, leading to a Denial-of-Service (DoS) attack. This phenomenon is known as jamming. However, security at this layer isn’t just about RF— the wired network that APs are plugged into can also be targeted, affecting APs directly or allowing rogue APs to be deployed on the same Layer 2 network.
That brings us one layer up to the MAC Layer. The security mechanisms at this layer are the ones I expect this book will help me learn the most about: WEP, TKIP, CCMP/AES, WPA1, WPA2, WPA3, 802.1X, and more. These protocols provide authentication and/or encryption, ensuring only authorized devices can connect while protecting data from being exposed. With 802.11w-2009, Protected Management Frames (PMF) were introduced, securing 802.11 management frames in addition to the existing encryption methods for data packets. It’s a good thing this “feature” is now enforced in WPA3, and more and more clients are finally supporting it.
At the Network Layer (L3), securing traffic often involves using a VPN, which encrypts data end-to-end and ensures that even if wireless traffic is intercepted, it remains unreadable. This adds another layer of security beyond what 802.11 encryption provides, protecting data from attacks on unsecured or public networks.
Layers 4 (Transport – TCP/UDP), 5 (Session – SQL, SIP, etc.), and 6 (Presentation – HTML, JPEG, etc.) aren’t the primary focus when it comes to wireless security, but they’re still worth exploring based on your own interests. Security is a vast and ever-evolving field, and there’s always something new to learn beyond just wireless networking.
Layer 7 (Application) is all about using secure protocols like HTTPS, SSH, SCP/SFTP, IMAPS, and DNSSEC, which rely on TLS or other cryptographic algorithms to encrypt traffic and keep data safe.
Wireless security isn’t just about slapping on WPA3 and calling it a day. It’s about knowing what threats exist, how they operate, and how to defend against them at every layer. Chapter 1 sets the stage for the rest of the CWSP journey, giving a solid foundation before we start tackling the more advanced security mechanisms. If you’re diving into CWSP, expect to rethink how you look at Wi-Fi security—it’s more than just encryption, it’s about strategy, design, and staying ahead of potential attacks. Looking forward to the deep dive in the next chapters!
Source(s):
Carpenter, T., et al. (2023). CWSP-207: Certified Wireless Security Professional Study Guide (1st ed.). Durham NC, USA: Certitrek Publishing
Wikipedia. (n.d.) Wired Equivalent Privacy. Retrieved January 29, 2025, from https://en.wikipedia.org/wiki/Wired_Equivalent_Privacy