Authentication is the cornerstone of Wi-Fi security. It’s no coincidence that it takes the first place in the AAA security model (Authentication – Authorization – Accounting). This chapter dives into how authentication works in Wi-Fi, from simple passphrases to advanced EAP implementations. However, one thing this chapter won’t cover is WPA3—that deserves a deep dive of its own.
What Is Authentication?
Authentication is the process of proving that a person or object (an identity) is who or what they claim to be. In its simplest form, authentication can be summarized in just three words: proof of identity. This is often confused with authorization, which is the process of controlling or granting access to specific resources after authentication has been verified. First, you prove who you are, then the system determines what you’re allowed to do.
Why use encryption?
The way authentication is implemented varies, but one crucial security principle is encryption. Even if you use biometric authentication or some other advanced method, if the authentication data is sent in clear text, an attacker could intercept and steal your credentials.
For this reason, credentials should always be hashed and protected in a way that makes them nearly impossible to crack. The 802.11 standard strictly prohibits transmitting credentials in clear text—except in WEP, where even though the credentials themselves aren’t visible, the challenge-response process is exposed in clear text, making it easy to break. As security has evolved, newer protocols like WPA3 introduce more robust encryption mechanisms to counter these vulnerabilities.
Wireless vs Wired Authentication
In more advanced AAA (Authentication, Authorization, Accounting) systems, a client can be identified based on multiple factors:
- Authentication method (802.1X/EAP)
- User identity
- Device identity
- Location
- Time of authentication
In wired networks, location-based authentication can be very specific—down to a switch port (e.g., a port leading to the CEO’s office). Since the switch is physically secured, this method is reliable.
In wireless networks, however, things get trickier. Identifying a client by AP association only provides a rough 3D location radius of at least a few hundred square meters. Even with triangulation, a device could still be located just outside the secured area—say, in a parking lot or nearby office. Since RF has no physical boundaries, authentication in WLAN environments is even more critical than in wired networks.
Choosing the Right Credentials
When securing a Wi-Fi network, one of the first steps in the process is choosing the right credentials. This selection process should consider the primary features of the credential solution and whether you need a multifactor authentication framework. Credential security relies on three pillars:
- How credentials are protected (e.g., hashing algorithms)
- Where credentials are stored (e.g., AP, controller, server, client certificate store)
- How credentials are accessed (e.g., LDAP, RADIUS)
MFA relies on multiple credential types:
- Something you know (e.g., passwords, PINs)
- Something you have (e.g., smart cards, certificates, security tokens)
- Something you are (e.g., fingerprints, retinal scans)
A common example is biometric authentication combined with a PIN—like unlocking your smartphone with a fingerprint scan, then entering a PIN. Another example is ATM security, where you need both a physical card and a PIN.
While MFA is gaining adoption, cyber threats continue to evolve, targeting weak points in authentication systems. This also doesn’t mean that when MFA is enabled, you’re fully protected.
The Role of Passphrases in Wi-Fi Security
Despite the rise of MFA, passphrases remain the most common authentication method. Even when using MFA, a passphrase is often still part of the equation.
The preferred cipher suites from the 802.11-2020 standard are CCMP (used in WPA2) and GCMP (used in WPA3). The preferred encryption algorithm is AES. Vendors will steer you to use these preferred methods by simply not allowing other weaker alternatives (like TKIP) to be configured by default.
Even with strong encryption, passphrase strength is critical. A passphrase is not the same as a PSK (Pre-Shared Key). Instead, the passphrase is converted into a PSK using a hashing process.
This process, as defined in 802.11-2020, follows:
- PBKDF2 (Password-Based Key Derivation Function 2)
- HMAC-SHA1 hashing algorithm
- 4096 iterations
More information about this process can be found in RFC2898.
Because the hashing process is static, the only variable is the passphrase. This is why passphrases must be strong and unique—otherwise, they are susceptible to dictionary attacks.
Dictionary attack
A dictionary attack is one of the most common methods used to crack WPA2-PSK. It works by systematically trying out a list of possible passwords. This type of attack involves following steps:
- Capture the Handshake:
First, the attacker captures the WPA2 handshake between the client device and the Wi-Fi access point. This handshake contains encrypted data that can be used to verify potential passphrases.
- Prepare the Wordlist:
The attacker uses a wordlist, which is a file containing a list of potential passwords. These wordlists can be created from common words, phrases, and known passwords, or downloaded from repositories.
- Hashing Process:
For each word in the dictionary, the attacker runs it through the PBKDF2 hashing algorithm with HMAC-SHA1, using the SSID as the salt and performing 4096 iterations. This process generates a 256-bit Pre-Shared Key (PSK).
- Verification:
The generated PSK is then compared to the hash in the captured handshake. If a match is found, the passphrase is cracked. If no match is found, the attacker may try another wordlist or use different attack methods.
Modern and specialized hardware like GPU’s can perform these calculations very quickly, and with a good wordlist your passphrase can be cracked in minutes if not seconds. Aircrack-ng (https://www.aircrack-ng.org/) is a popular tool for Wi-Fi security testing including dictionary attacks. Please ensure you use this tool ethically and responsibly.
Private PSK (PPSK)
One major downside of traditional WPA2-Personal is that one shared password grants full network access. The introduction of Private PSK (PPSK) helps mitigate this risk by allowing multiple passphrases—or even per-user passphrases—for accessing the same SSID.
With PPSK, each passphrase can be tied to different access groups and VLANs, bridging the gap between WPA2-Personal and WPA2-Enterprise in terms of role-based access control. This means different users or device types can have different levels of access, even though they connect to the same SSID.
However, it’s important to note that:
- PPSK implementations vary by vendor, and some don’t support it at all.
- PPSK is NOT a replacement for 802.1X/EAP—it’s still susceptible to dictionary attacks if an attacker captures the right 4-way handshake.
What Makes a Strong Password?
The key factor in password security is entropy—which represents the randomness and unpredictability of a password. Entropy is measured in bits using the formula:
E = L × log2(R)
Where:
- E = entropy in bits
- R = number of possible characters
- L = length of the password
It’s recommended to use at least 72-bit entropy for strong passphrases. This translates to:
- A minimum of 11 characters if using letters, numbers, and special characters (R = 94).
- A minimum of 12 characters if using only letters and numbers (R = 62).
However, as computing power increases, an 11-character passphrase can now be cracked in significantly less time than it could a few years ago. For highly sensitive accounts, a 128-bit entropy password is advised—requiring at least 20 characters.
When you see a password strength bar while creating a new password, it often reflects entropy levels rather than just length.
WPA2-Enterprise
Despite advancements like PPSK, the go-to for securing Wi-Fi networks remains WPA2-Enterprise (and WPA3-Enterprise). This is mainly due to two critical security advantages:
- Mutual Authentication:
- Both the client and authentication server verify each other’s identity.
- Prevents rogue authentication servers from tricking clients into connecting to fake SSIDs.
- Typically implemented using domain certificates.
- Dynamic Encryption Keys:
- Unlike PSK, where everyone shares the same key, 802.1X dynamically generates unique encryption keys per session.
- Even if one session key is compromised, it doesn’t affect other users.
Role-Based Access Control (RBAC) with 802.1X
Another major benefit of WPA2-Enterprise is the flexibility of role-based access control (RBAC). Based on the user’s authentication credentials, the system can dynamically assign:
- Different VLANs
- Access Control Lists (ACLs)
- Firewall rules
- Bandwidth limitations
- QoS settings
This is where the second “A” in AAA comes into play: Authorization—determining what a user can or cannot do on the network.
The final “A” in AAA is Accounting, which allows administrators to track user activity on the network. The RADIUS client (AP, switch, or WLC) is responsible for sending event-based updates or statistics to the RADIUS server. The RADIUS server may also periodically request updates using a “status-server” message to ensure session validity.
802.11 Robust Security Network Association
To establish an RSNA, a Wi-Fi client must first authenticate and associate with the network. During this phase, the RSN Information Element (RSN IE) is exchanged, where the AP specifies the Authentication and Key Management (AKM) Suite that will be used. This suite determines whether the network is WPA2, WPA3, and whether it operates in Personal or Enterprise mode.
If Fast Transition (802.11r) is enabled, a different AKM suite will be indicated for roaming purposes—something we covered during CWAP studies. Understanding this exchange is important, especially when troubleshooting connectivity issues related to 802.1X authentication failures or roaming handoffs between APs.
802.1X Port states
The second step in 802.1X authentication is mutual authentication between the supplicant (client) and authentication server. To understand this process, we need to look at 802.1X port states.
An 802.1X port consists of two virtual states:
- Uncontrolled Port: Initially, a newly associated client connects through this port. No data traffic is allowed, meaning the client won’t even get an IP address at this stage. This state is only used in the authentication process.
- Controlled Port: Once authentication is successfully completed, this port opens, allowing the client to send protected data.
In a Wi-Fi environment, this process is handled virtually rather than being a physical port, unlike in wired networks where 802.1X operates on a physical switch port. The AP (or WLAN controller) acts as the Authenticator, forwarding the 802.1X/EAP credentials to the RADIUS server for authentication.
This distinction is crucial because 802.1X is not a direct authentication between the client and AP—the AP is merely the middleman that passes authentication requests between the supplicant (client) and the authentication server (RADIUS). This is why misconfigurations on the RADIUS server or connectivity issues between the AP and the authentication server can often cause 802.1X failures.
The Pairwise Master Key (PMK) and 4-Way Handshake
Once mutual authentication is completed, both the supplicant and authentication server must have matching Pairwise Master Keys (PMKs). This PMK is generated during the 802.1X/EAP authentication process.
At this point, the uncontrolled port remains open, but the controlled port is still blocked until the 4-way handshake is successfully completed. This handshake process derives a Pairwise Transient Key (PTK) from the PMK, ensuring that each session is encrypted with a unique key.
From here, the process follows the same 4-way handshake as in WPA2-Personal, securing the communication by generating unique encryption keys per session. More details on this process can be found in one of my previous blog posts (CWAP Chapter 5).
Common EAP Types in Wi-Fi
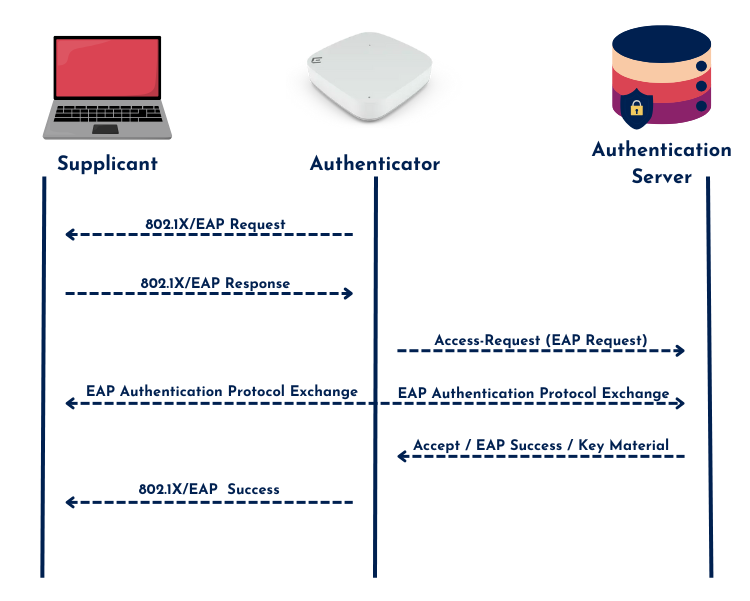
There are several EAP (Extensible Authentication Protocol) methods available, but the two most widely used for Wi-Fi authentication are EAP-PEAP and EAP-TLS. 802.1X/EAP authentication follows a structured sequence, as illustrated in the Basic EAP Framework below.
| Feature | EAP-TLS | EAP-PEAP |
| Mutual Authentication | Yes | Yes |
| Certificates Required | Client/Server | Server Only |
| Dynamic Key Generation | Yes | Yes |
| Costs and Management Overhead | High | Medium |
| Industry Support | High | High |
- EAP-TLS is considered the gold standard for authentication—if the environment allows for setting up and maintaining a Public Key Infrastructure (PKI). With both client and server certificates, it offers strong security but comes with higher deployment complexity and costs. This makes it the preferred choice in high-security environments, such as government or financial institutions.
- EAP-PEAP (Protected EAP) first sets up a TLS tunnel using server certificate validation, after which an inner EAP method is used for authentication.
- PEAPv0 supports EAP-MSCHAPv2 (username/password) or EAP-TLS inside the tunnel.
- PEAPv1 supports EAP-GTC, mainly used with tokens or smartcards (e.g., RFID cards).
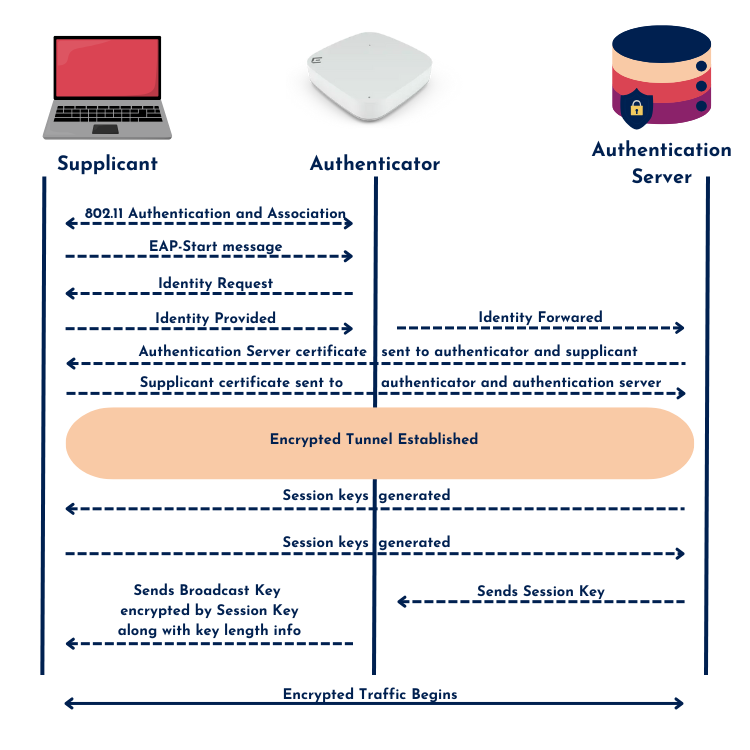
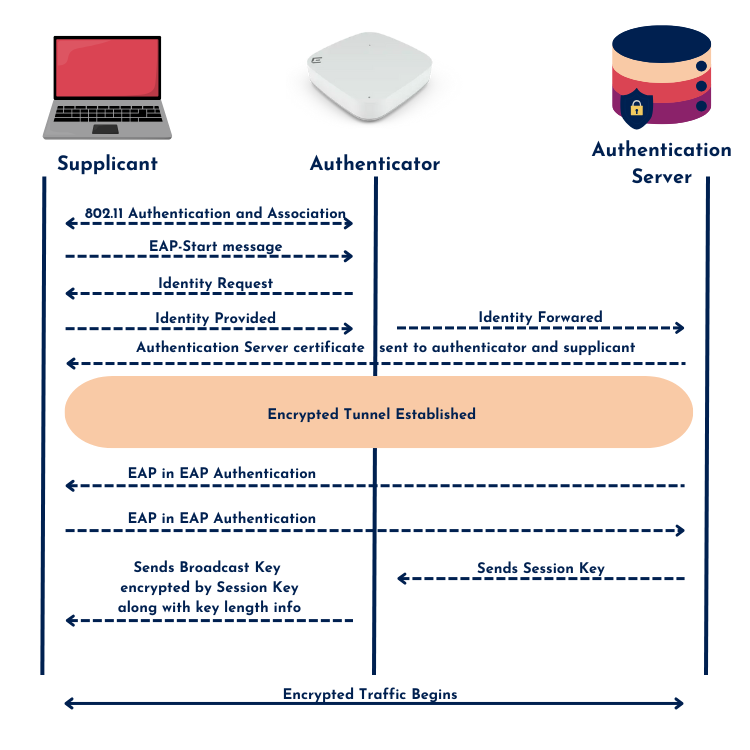
PEAP is widely used because it only requires a server certificate, making it easier to deploy than EAP-TLS, which requires both client and server certificates. That said, PEAP-MSCHAPv2 still relies on password authentication, which introduces potential security risks if credentials are weak or improperly stored.
To be fair, EAP-PEAP with EAP-TLS as the inner method isn’t something you see often. It adds an extra layer of encryption but doesn’t necessarily improve security beyond standard EAP-TLS, since both methods already use TLS certificates. The main drawback of layering PEAP over EAP-TLS is that it introduces extra processing steps, which can lead to longer roaming times—a dealbreaker in latency-sensitive environments like VoIP over Wi-Fi.
However, some organizations still use it as an added security measure to ensure that client devices always authenticate within a secure tunnel, especially in multi-vendor deployments where direct EAP-TLS authentication might not be consistently supported across different client devices.
Conclusion
Authentication is the foundation of Wi-Fi security, and choosing the right method makes all the difference. From simple PSKs to enterprise-grade 802.1X authentication, each approach has its own strengths and weaknesses. While WPA2-Enterprise with EAP-TLS is the gold standard, other methods like PEAP can still offer a solid balance between security and usability.
Understanding how authentication works—whether it’s the 4-way handshake, mutual authentication, or encryption key management—helps in designing more secure and efficient wireless networks. With evolving threats, security practices should continuously be reviewed, ensuring that networks are not just protected, but also scalable and resilient.
If you’re studying for CWSP or simply aiming to strengthen your network security knowledge, keep digging into authentication, encryption, and access control. As always, feel free to reach out if you have any thoughts, questions, or insights!
Source(s):
Carpenter, T., et al. (2023). CWSP-207: Certified Wireless Security Professional Study Guide (1st ed.). Durham NC, USA: Certitrek Publishing