Encryption is defined as the process of modifying information (data) with an algorithm (cipher) that results in unreadable or meaningless data to those without the key used in the algorithm. As with previous chapters, this one is not diving into WPA3. I believe we’re in for a treat in chapter 10. We will discuss how encryption works and in which forms they come.
Symmetric Key Encryption
Two common encryption techniques used in the digital world are symmetric and asymmetric key encryption. Symmetric key encryption is the primary method used in today’s wireless networks. Both parties need to possess the same key—or at least part of it—to encrypt and decrypt information.
In WPA2-Personal, for example, this key is the passphrase. While the passphrase itself is never transmitted over the air, other keying material like the ANonce and SNonce is. As we’ve discussed earlier, this opens up some vulnerabilities—such as the possibility of dictionary attacks. Once an attacker captures a 4-way handshake, simply knowing the passphrase is enough to decrypt wireless traffic.
As the name suggests, symmetric means equal: both ends use the same information to secure communication.
Asymmetric Key Encryption
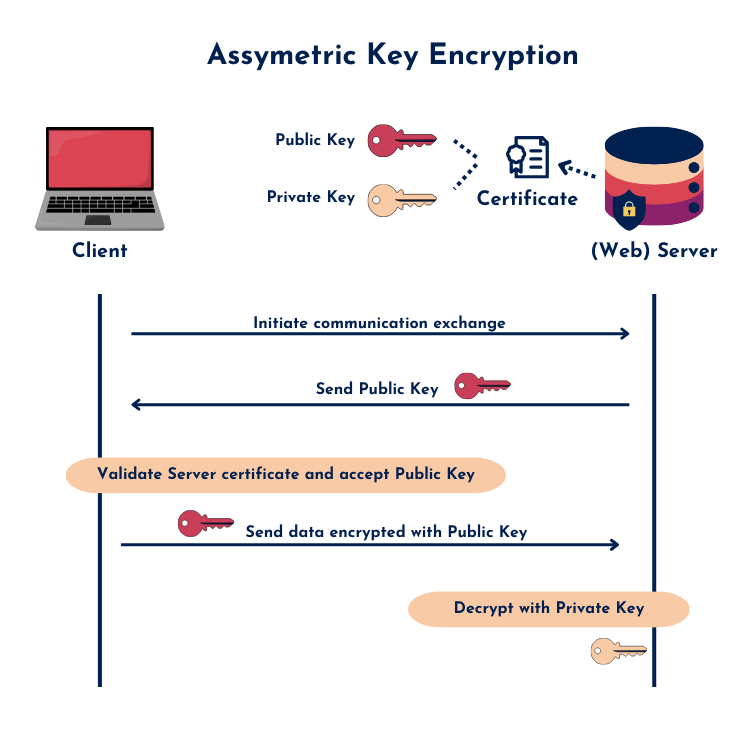
Asymmetric encryption, on the other hand, means not symmetric—not equal. This method uses a different key for encryption than for decryption. It’s often referred to as public-key cryptography.
Here’s how it works:
- The server holds:
- A public key (shared with anyone)
- A private key (kept secret)
- The client receives the server’s public key—usually through a digital certificate (like in HTTPS).
- The client encrypts a message (for example, a session key) using the public key.
- The encrypted message is sent to the server.
- The server uses its private key to decrypt the message.
A commonly used analogy: imagine the public key as an open padlock and the private key as the only key that can unlock it. The server sends out this open padlock to the client. The client puts the message inside a box, locks it with the padlock, and sends it back. Now, only the server—with the correct private key—can open that box.
This principle is used in certificate-based security, like HTTPS. The public key inside the server’s certificate is used by the client to encrypt the session key. Only the web server—who holds the private key—can decrypt it and establish a secure channel.
To take it a step further, mutual authentication can be used. In this case, it’s not just the client trusting the server’s certificate—the server also verifies a certificate from the client, as seen in EAP-TLS. This offers much stronger authentication and is especially relevant in securing wireless networks.
Ciphers
A cipher is a mechanism that enables the encryption and decryption of information. In 802.11, we typically distinguish between two types: stream ciphers and block ciphers. A stream cipher works by encrypting one bit at a time, usually through an XOR operation. This is the process used with WEP and TKIP, which I’ve already touched on in my blog post for CWSP Chapter 1.
The cipher algorithm itself isn’t necessarily the weakest link (though far from ideal), but the main issues with WEP lie in its short Initialization Vector (IV) and Integrity Check Value (ICV). These weaknesses lead to IV reuse and predictability, which, combined with the XOR-based encryption process, allow attackers to eventually derive the WEP key.
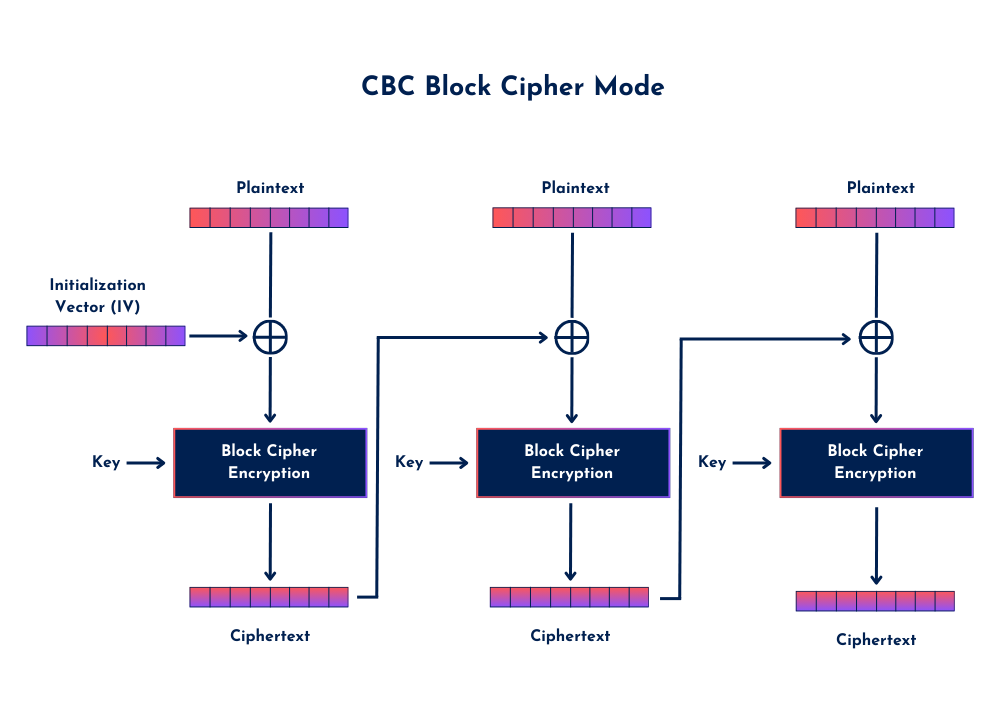
In contrast to stream ciphers, block ciphers encrypt plaintext data in blocks (or chunks) of bits, instead of encrypting one bit at a time. The type of block cipher defines the size of the block that is processed. CCMP/AES, for example, uses a 128-bit block size. The mode that it operates in is Cipher Block Chaining (CBC), where each plaintext block is XOR’d with the previous ciphertext block before encryption.
The first block of plaintext is XOR’d with a random Initialization Vector (IV) before being encrypted. After that, every subsequent block uses the ciphertext of the previous block as part of its encryption process. This method ensures that identical plaintext blocks will encrypt differently, strengthening the security of the data stream.
Even though the IV is transmitted in clear text (which is normal), the strength of AES encryption ensures that an attacker cannot simply capture the first encrypted block and derive the encryption key. Capturing a single ciphertext block, or even multiple blocks, does not expose the encryption key or allow the plaintext to be revealed without significant cryptographic breakthroughs. Additionally, if any block is altered, it impacts the decryption of subsequent blocks, providing an extra layer of protection against tampering.
Encryption in Wi-Fi
Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext), so that only authorized parties with the correct decryption key can make sense of it. In wireless networking, this is essential for keeping your over-the-air traffic confidential and protected from tampering.
The earliest encryption method used in Wi-Fi was WEP, which relied on the RC4 stream cipher. As discussed in Chapter 1, WEP was fundamentally flawed — mainly because of its short initialization vector (IV) and predictable key reuse. To patch these vulnerabilities, TKIP (Temporal Key Integrity Protocol) was introduced alongside WPA (Wi-Fi Protected Access) as a stopgap before WPA2. TKIP still used RC4, but added some improvements like per-packet key mixing, a message integrity check (MIC), and dynamic rekeying — meaning the encryption keys changed more often. These changes did improve security over WEP, but TKIP came with a price: more processing overhead and, ultimately, it still wasn’t strong enough for long-term use. Today, TKIP is deprecated and should not be used in modern Wi-Fi networks.
That’s where AES (Advanced Encryption Standard) came in, bringing a much stronger and more efficient encryption option. But AES isn’t used on its own — it’s implemented through cipher suites. In WPA2 networks, the most widely used and important one is CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol). CCMP uses AES in two ways: it applies Counter (CTR) mode for data confidentiality (the actual encryption), and CBC-MAC for integrity and authentication. So, not only is the data encrypted, but it’s also protected from tampering along the way.
CCMP/AES has been the go-to for WPA2-secured networks and still holds its ground today. WPA3 introduces GCMP as a newer, faster alternative — but more on that in Chapter 10. For now, just know that CCMP adds strong, reliable encryption and message integrity that was missing from older methods like TKIP and WEP.
One last thing to keep in mind — if you’re still running into networks that use TKIP (like in those rare transition mode setups), remember that TKIP limits the maximum MCS rate to just 54 Mbps, dating all the way back to the 802.11a/g era. That’s because TKIP isn’t compatible with the higher throughput features of 802.11n and beyond. So if you’re troubleshooting a slow connection and spot TKIP in the RSN Element — that might just be your culprit. It’s been deprecated since the 802.11-2012 standard, so hopefully we’ve all moved on by now.
Okay, so that wraps up our chapter on encryption. We didn’t dive into cryptographic equations or start solving hash collisions—but that wasn’t the point either. This chapter was all about understanding how encryption fits into Wi-Fi security, how different keys and cipher types work together, and why legacy stuff like WEP and TKIP should really be left behind. WPA2 with CCMP/AES has been holding the line for quite a while now, and although it’s not without its limitations, it still forms the core of most enterprise Wi-Fi security today.
There’s more to come—WPA3 and GCMP will get their own spotlight in Chapter 10. For now, it’s just important to understand the building blocks and why proper encryption matters. Because if you don’t understand what’s going on behind the scenes, it’s hard to make the right choices when designing or troubleshooting a secure wireless network.
Source(s):
Carpenter, T., et al. (2023). CWSP-207: Certified Wireless Security Professional Study Guide (1st ed.). Durham NC, USA: Certitrek Publishing